Site blog
In the digital age, the importance of cybersecurity cannot be overstated. Phishing scams pose a significant threat to individuals and businesses alike. To combat this menace, the Federal Trade Commission (FTC) has created an interactive and educational tool known as the OnGuard Online Phishing Scams Game. This game not only entertains but also equips users with the knowledge and skills necessary to identify and avoid phishing scams. In this article, we will explore the game's purpose, how it operates, and the significance of understanding phishing in today's world.
The Purpose of OnGuard Online
OnGuard Online is an initiative led by the FTC to provide resources for individuals looking to protect themselves from various online threats. The site offers practical tips, resources, and interactive solutions designed to educate users about cybersecurity. One of the standout features of the website is the Phishing Scams Game, which allows players to learn about phishing scams through an engaging and relatable medium.
What is Phishing?
Phishing is a form of cybercrime where attackers deceive individuals into providing sensitive information such as usernames, passwords, credit card numbers, and other personal details. This is often achieved through seemingly legitimate emails or messages that mimic trustworthy sources. By clicking on malicious links or providing information, victims unwittingly reveal their data to criminals, leading to identity theft and financial losses.
How the Game Works
The OnGuard Online Phishing Scams Game leverages interactive storytelling to educate players. The game presents various scenarios where players must identify whether a message is a phishing attempt or a legitimate communication. As they proceed, players are given subtle hints and information regarding the nature of phishing scams.
- Scenario-Based Learning: Each level introduces a new scenario, such as an email from a bank asking for verification or a message claiming the user has won a prize. Players must analyze these communications critically to determine their authenticity.
Benefits of Playing
The OnGuard Online Phishing Scams Game offers numerous benefits for individuals of all ages. Here are a few compelling reasons to engage with this educational tool:
- Enhancing Critical Thinking: The game encourages players to think critically about the messages they receive online. This enhanced awareness can translate into better decision-making when navigating the internet.
The Importance of Awareness
In conclusion, the FTC's OnGuard Online Phishing Scams Game serves as an essential tool in the ongoing fight against cybercrime. By familiarizing users with the tactics employed by scammers and equipping them with knowledge to identify phishing attempts, the game plays a crucial role in enhancing cybersecurity awareness. As phishing scams continue to evolve, ongoing education and awareness will remain vital in protecting personal and financial information. The lessons learned from this game not only prepare individuals to defend against phishing but also contribute to a more secure internet for everyone.
In the age of digital communication, online phishing has emerged as one of the most persistent and damaging threats to personal and organizational security. Phishing is a form of cybercrime where attackers attempt to deceive individuals into providing sensitive information such as usernames, passwords, credit card numbers, and bank details. This article will delve into the mechanics of phishing attacks, their various forms, the impact they have on individuals and organizations, and measures that can be taken to protect against such threats.
What is Phishing?
Phishing typically involves an attacker masquerading as a trustworthy entity in electronic communications. The most common vector for phishing attacks is email, where the attacker sends messages that appear to be from legitimate sources, such as banks, online service providers, or well-known brands. These emails often contain links to fraudulent websites designed to look like the legitimate ones, tricking victims into entering their personal information.
While phishing is historically linked to email, the problem has evolved over the years. Attackers now use various methods to reach victims, including social media platforms, instant messaging, and even phone calls, adding a layer of complexity to detection and prevention.
Different Types of Phishing
- Spear Phishing: Unlike traditional phishing attacks that target a large number of people, spear phishing is personalized and aims at specific individuals or organizations. Attackers may gather information from social media profiles or other publicly available resources to create tailored messages that increase the likelihood of success.
The Impact of Phishing
The consequences of phishing can be severe. For individuals, falling victim to a phishing attack can result in identity theft, financial loss, and significant emotional distress. For organizations, the ramifications are even graver—data breaches can lead to substantial financial losses, erosion of customer trust, legal penalties, and damage to brand reputation. According to a report from cybersecurity firms, phishing accounts for a majority of data breaches. Organizations have found themselves investing heavily in cyber defense mechanisms as a direct response to these threats.
Recognizing Phishing Attempts
Spotting a phishing attempt can be challenging, especially as attackers constantly refine their techniques. However, there are several red flags that can help individuals and organizations identify potential phishing attempts:
- Unusual Sender Email Addresses: Attackers often create email addresses that closely resemble legitimate ones but may contain subtle misspellings or additional characters.
Prevention Measures
To effectively combat phishing, individuals and organizations must adopt a proactive approach. Here are some best practices:
- Education and Training: Regular training sessions on identifying phishing attacks can equip employees with the knowledge they need to recognize threats before they escalate.
Conclusion
As the digital landscape continues to evolve, so do the tactics employed by cybercriminals. Phishing remains one of the most common and dangerous forms of cyberattacks, but by understanding the methods used, recognizing warning signs, and implementing effective preventive measures, both individuals and organizations can defend against this pervasive threat. Awareness and vigilance are essential in safeguarding sensitive information in today's interconnected world.
Phishing attacks have become one of the most prevalent threats on the internet today, compromising sensitive information and personal data of millions of users. In an era where digital transactions and online interactions are commonplace, having a reliable security tool is crucial for safeguarding users against such malicious activities. Avast Online Security is one such tool that plays an essential role in protecting users against phishing attempts. In this article, we will explore how Avast identifies and blocks phishing sites, the implications of such protective measures for users, and best practices for maintaining online security.
What is Phishing?
Phishing is a cybercrime in which attackers impersonate a legitimate organization or individual to trick victims into providing sensitive information, such as usernames, passwords, credit card details, or personal identification numbers. This is often done through deceptive emails, websites, or text messages that appear authentic. Phishing can take various forms, including email phishing, spear phishing (targeted attacks), and vishing (voice phishing). Each method relies on manipulating human psychology to elicit trust and persuade individuals to share confidential information.
Role of Avast Online Security
Avast Online Security is a powerful browser extension that enhances users’ online safety by providing real-time protection against various online threats, including phishing. When users navigate the internet, Avast employs advanced algorithms and a constantly updated database of known phishing sites to determine the safety of the pages being visited.
How Avast Detects and Blocks Phishing Sites
- Database of Known Threats: Avast maintains a comprehensive database of websites known for phishing activities. This database is continuously updated based on data aggregated from millions of users and threat intelligence sources. When a user attempts to visit a site, Avast cross-references it against this database to identify potential threats.
Implications of Blocking Phishing Sites
The ability of Avast Online Security to block phishing sites has significant implications for users. First and foremost, it helps prevent identity theft and the unauthorized use of personal information. In a digital landscape where personal data is often the currency of social interactions and transactions, protecting this data is paramount.
Moreover, Avast’s phishing protection promotes a safer browsing experience. By providing real-time alerts and blocking malicious websites, users can explore the internet with greater confidence, knowing there is a layer of security in place. This peace of mind allows individuals to engage in online shopping, banking, and communication without fear of falling victim to scams.
Best Practices for Online Security
While tools like Avast Online Security are instrumental in protecting against phishing attacks, users should also adopt best practices to enhance their online security. Here are some recommendations:
- Stay Informed: Familiarize yourself with the latest phishing tactics and scams. Cybercriminals constantly evolve their methods, and awareness is one of the best defenses.
Conclusion
In an age where digital threats are omnipresent, Avast Online Security serves as a reliable ally in the fight against phishing attacks. By blocking harmful sites and providing real-time alerts, it empowers users to maintain their online security effectively. However, users should remain vigilant and adopt a proactive approach to their cybersecurity practices. By combining the protection offered by Avast with sound cybersecurity habits, individuals can navigate the online world safely and confidently.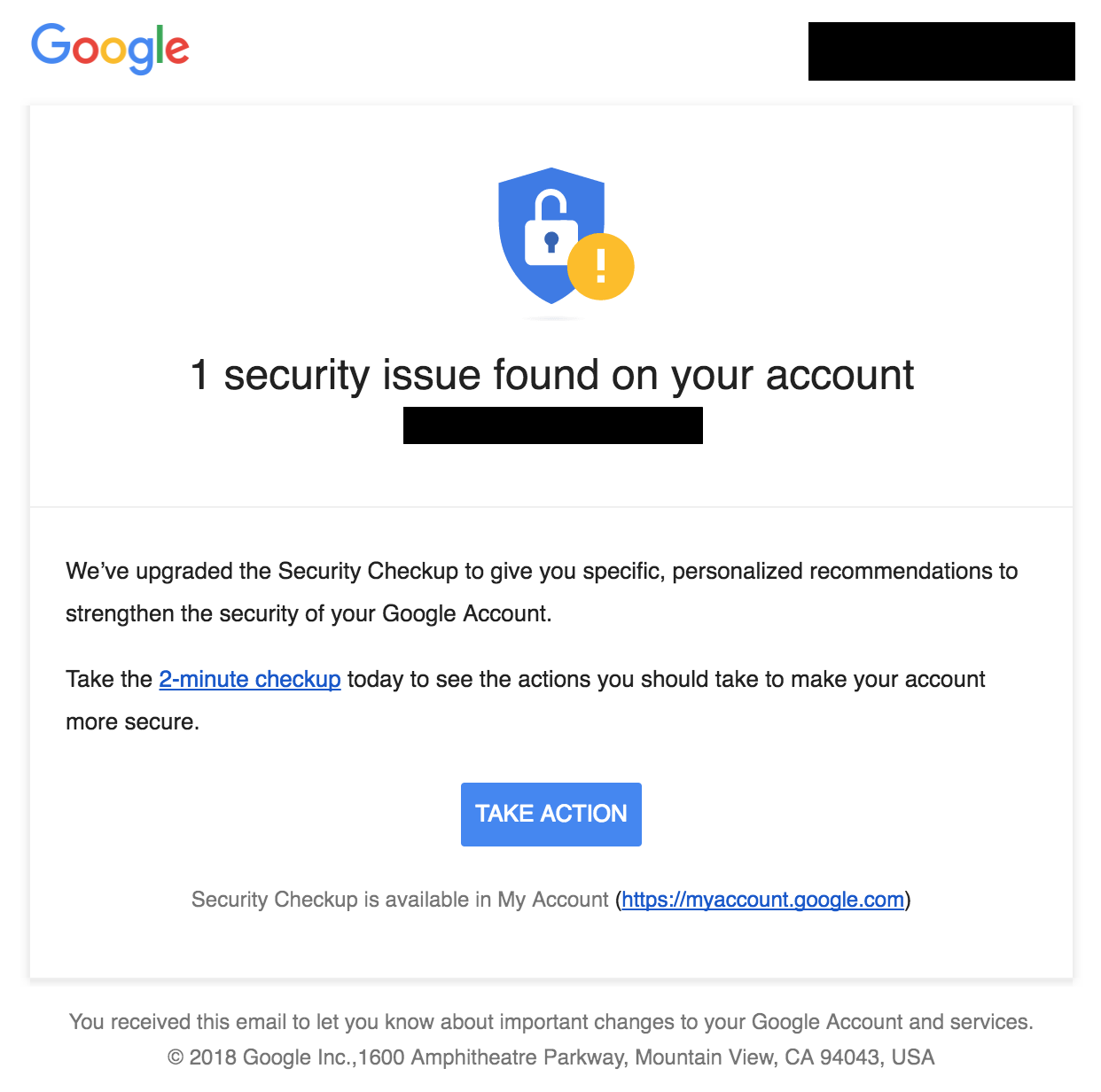
Phishing is a form of cybercrime that involves deceiving individuals into providing sensitive information such as usernames, passwords, GOOGLE DELETE PHISING credit card details, and other personal data. This malicious tactic has evolved over the years into a sophisticated method of attack that leverages social engineering and technological advancements to exploit human emotions like fear, curiosity, and trust. As the internet continues to grow, so does the prevalence of phishing attacks, making it imperative for users to understand the nature of this threat, the techniques employed by attackers, and the methods for protection.
The term "phishing" is derived from the word "fishing," implying that cybercriminals are casting a net to catch unsuspecting victims. Typically, phishing involves the use of fraudulent emails or websites designed to appear legitimate, often mimicking well-known organizations such as banks, online services, or social media platforms. These communications usually contain urgent messages that prompt users to click on malicious links, which lead to sites that resemble authentic web pages.
One common type of phishing attack is spear phishing, where attackers target specific individuals or organizations with personalized messages. This approach increases the likelihood of success because the attackers gather information about their victims beforehand, making the content more convincing. For instance, they may reference current projects, mutual acquaintances, or legitimate business accounts, creating a false sense of security.
Another variant is whaling, which specifically targets high-profile individuals within organizations, such as executives or senior management. By using highly tailored messages, whaling attacks aim to extract sensitive corporate information or initiate fraudulent wire transfers. Given the potential financial repercussions and reputational damage, whaling poses a significant risk to companies and their stakeholders.
Phishing has also expanded beyond email, with the emergence of SMS phishing (smishing) and voice phishing (vishing). Smishing involves sending fraudulent text messages that prompt users to provide personal information or click on malicious links. Vishing, on the other hand, is executed through phone calls that impersonate legitimate entities, such as banks or government agencies. These methods leverage technology to reach individuals directly, increasing the persuasion factor in the communication.
The impact of phishing attacks can be severe. Victims may suffer financial losses, identity theft, and unauthorized transactions, while companies can face legal repercussions, loss of customer trust, and data breaches that compromise sensitive corporate information. According to the Anti-Phishing Working Group (APWG), phishing attacks have increased dramatically, with millions of phishing websites reported each year. This growth indicates a pressing need for effective countermeasures.
To combat phishing, it is essential for individuals and organizations to implement robust security practices. One of the first steps is to educate users about the risks associated with phishing and how to recognize potential threats. This education includes training programs that cover the common signs of phishing attempts, such as misspelled URLs, generic greetings, and suspicious attachments.
Another critical measure is the adoption of multi-factor authentication (MFA). MFA provides an additional layer of security by requiring users to confirm their identity through multiple means—such as a password followed by a unique code sent to their mobile device—making it more challenging for cybercriminals to gain unauthorized access.
Regularly updating software and security systems is also crucial. Organizations should ensure that all applications, operating systems, and anti-virus software are kept up to date to protect against known vulnerabilities exploited by attackers. Moreover, utilizing advanced email filtering solutions can help detect and block phishing attempts before they reach the user's inbox.
For individuals, verifying the authenticity of communications is vital. Users should take the time to hover over links to inspect their URLs before clicking, avoid providing personal information in response to unsolicited requests, and be vigilant about any correspondence that evokes a sense of urgency or fear. When in doubt, contacting the organization directly using official contact methods can help confirm the legitimacy of the communication.
In conclusion, phishing is a pervasive cyber threat that can lead to significant financial and personal losses if left unchecked. As technology continues to evolve, so do the tactics employed by cybercriminals. Therefore, understanding the nature of phishing, recognizing its various forms, and implementing effective security measures are essential in protecting oneself and one’s organization from this growing threat. Through education and vigilance, individuals and companies can significantly mitigate the risks associated with phishing and maintain a secure online environment.
In recent years, online scams have proliferated, with phishing being one of the most common threats faced by internet users. To address this growing concern, the Federal Trade Commission (FTC) has developed the "On Guard Online" platform, which includes an interactive game designed to educate users about phishing scams. This article presents an observational study of this game, focusing on its educational value, user engagement, and potential for raising awareness about phishing attacks.
The "On Guard Online" game allows users to navigate through a series of simulated email scenarios where they must identify phishing attempts. Players are presented with various email messages, some of which contain genuine content while others are designed to deceive. The objective is to recognize the red flags associated with phishing attacks, such as suspicious links, generic greetings, and urgent requests for personal information. Participants are scored based on their ability to discern legitimate communications from fraudulent ones.
Observational research techniques were employed during gameplay sessions with a group of ten participants—five high school students and five adults. The data collection included noting the time taken to complete the game, the choices made by each participant, and their discussions during the gameplay. Participants were encouraged to think aloud and articulate their thoughts regarding the emails presented. This qualitative approach allowed us to gain insights into their cognitive processes and strategies when identifying phishing attempts.
The preliminary findings suggest that the game is effective in engaging users and enhancing their understanding of phishing tactics. Participants demonstrated heightened awareness while progressing through the game. High school students displayed a commendable ability to recognize numerous phishing elements, often discussing their thought processes with enthusiasm. Some students voiced concerns over how realistic and relatable the scams felt, demonstrating that they understood the implications of phishing beyond simply recognizing fraudulent emails.
Adults in the group, however, exhibited different levels of confidence and familiarity with online scams. While some adults swiftly identified deceptive emails, others expressed hesitation and uncertainty. Notably, participants who reported prior experiences with phishing scams were more adept at spotting potential threats. This variation in performance highlights the importance of experience in recognizing phishing attempts and underscores the need for ongoing education regardless of age.
One interesting observation involved the emotional responses elicited during gameplay. Participants expressed feelings of frustration when they failed to identify phishing attempts and excitement when they successfully navigated a tricky email. This suggests that the game could be effectively utilized as both an educational tool and an engagement strategy that makes learning about online safety enjoyable.
The game's design, which incorporates interactive elements, colorful graphics, and real-life scenarios, contributes to its effectiveness as a teaching tool. Participants appreciated the user-friendly interface, making it accessible for players of varying ages and technological proficiency. The interactive nature of the game encouraged repeated play; many participants indicated they would return to strengthen their skills further.
Despite its strengths, there are areas for improvement. Although the game covers fundamental aspects of phishing scams, there is potential for expanding content to include other online safety tips, such as safeguarding social media accounts and recognizing different forms of scams. Additionally, incorporating a feedback mechanism could enhance learning; providing explanations for why certain emails were categorized as phishing would deepen understanding.
Overall, the observations made during this study underline the necessity of proactive measures in combating phishing scams. As cyber threats evolve, the need for effective education continues to grow. The FTC's "On Guard Online" phishing scams game is a commendable step towards empowering users with knowledge and skills to protect themselves online. It effectively fosters critical thinking and situational awareness, equipping participants with the tools needed to navigate the digital landscape securely.
In conclusion, while the "On Guard Online" phishing scams game has proven to be a valuable resource for raising awareness and educating users about the nuances of online fraud, there is ongoing room for GOOGLE DELETE PHISING enhancement. As the landscape of cyber threats changes, educational tools must adapt and innovate to provide comprehensive, relevant experiences for users. Continued observational research into user interactions will be essential in refining these approaches, ultimately creating a safer online environment for all.
Similarly, hopping back and forth between generic and name-brand medications could get complicated because of differences in formulation that have nothing to do with the active ingredient. It may get more relaxed as it acclimates to the experience. If you're traveling by motorcycle with your pet for the first time, you may want to try a shorter trip. See how your pet reacts. Conditions such as obesity, high blood pressure, anxiety, depression, chronic stress, heart disease, and diabetes are just a few of the conditions in the body that can lead to ED.
Ravnskov said that it all started with the landmark Framingham Heart Study, which began following healthy people in the early 1950s to see who had a heart attack and what distinguished them from the people who did not. The administrator may unlock this page, but it is not recommended -- somebody could come along and lock all non-administrators out by using a single dot as the regular expression. And if your lenses get scratched in the first 365 days, you can get new lenses made for free.
In the recommended single-dose range (25-100 mg), the use of Viagra for erectile dysfunction, in the absence of contraindications, is extremely safe provided the drug is taken under proper conditions $5 to $50) that you have to pay when you get medical care, instead of the regular bill (which your insurance company will pay for you). A copay is a flat fee (usually small, e.g. Coinsurance is the same thing as a copay, except a percentage (e.g.
All frontal crash tests in the United States are conducted using the same type of dummy, the Hybrid III dummy. 20%) instead of a flat fee. This was one of two supercars that proved to the world that hybrid technology could, in fact, be used to create an exhilarating experience for the driver. For example, if your plan says it has a $50 copay, then that means that you pay $50 every time you get medical care, and insurance gets the rest-even if the rest is thousands of dollars.
Some of the most iconic toys of the last century have been made by Hasbro. I don't have the time to list all the links--do your own research. If you have any thoughts pertaining to exactly where and how to use viagra online price, you can get in touch with us at our site. This gap was borne out by Consumer Guide® in a six-month evaluation of a 2004 Honda Civic Hybrid with automatic transmission Note though that some plans may offer a copay for certain services even before you have hit your deductible. Very active dogs or sight hounds may chase anything that moves. It's true that a person could hurt themselves in the case of hasty, improper use, but it's still better to have them than not.
There are printers that print much faster, but you will have to pay far more to own one. Again, let’s assume that all examples have a $1000 deductible and a $5000 out-of-pocket-maximum. Note that you may never actually hit your out-of-pocket maximum for the year, or sometimes even your deductible. Just like medications for humans, there are also some counterfeit pet meds being offered in some stores and this is particularly true when you buy through online outlets.
 Oh yeah, and just to make things more confusing, sometimes you can have different deductibles for different kinds of healthcare expenses.
Oh yeah, and just to make things more confusing, sometimes you can have different deductibles for different kinds of healthcare expenses.
Как превратить хаос ремонта в идеальную чистоту: секреты уборки
Пыль, пятна, хаос: как справиться с беспорядком после ремонта?
Ремонт — это шаг к мечте о новом доме, но что делать с горами пыли, пятнами краски и строительным мусором, которые остаются после? Уборка после ремонта может стать настоящим кошмаром, если не знать, с чего начать. Хотите превратить хаотичное помещение в сияющий уют? Мы раскроем секреты, которые помогут вам справиться с этой задачей без стресса. А для полного погружения в тему загляните в подробное руководство на сайте https://kliningekb.ru/kak-pravilno-splanirovat-i-organizovat-uborku-pomeshheniya-posle-remonta/
— там вы найдёте всё, чтобы уборка стала проще!
Секреты идеальной уборки: от пыли до блеска
Чтобы уборка после ремонта не превратилась в бесконечный марафон, следуйте этим шагам, которые используют профессионалы:
Подготовьтесь как профи. Соберите пылесос, тряпки из микрофибры, моющие средства и прочные мешки для мусора. Стремянка и перчатки тоже пригодятся. Оцените масштаб: где пыль, где пятна? Это ваш план атаки.
Сухая уборка — первый шаг. Пылесос — ваш лучший друг. Пройдитесь по потолку, стенам, углам. Пыль после ремонта коварна и прячется везде. Сухая тряпка из микрофибры соберёт остатки.
Борьба с пятнами. Краска, клей, цемент? Для каждого пятна есть свой лайфхак. Свежую краску смойте влажной тряпкой, клей уберите уксусом, а для цемента используйте слабый раствор кислоты (но осторожно!).
Влажная уборка для финального штриха. Мойте полы, окна, протирайте двери и подоконники. Используйте средства, подходящие для поверхностей, чтобы не осталось разводов. Работайте сверху вниз, чтобы пыль не оседала на чистое.
Эти шаги — лишь часть рецепта идеальной уборки. Хотите узнать, как справляться с самыми сложными загрязнениями и сэкономить время? Перейдите на https://kliningekb.ru/kak-pravilno-splanirovat-i-organizovat-uborku-pomeshheniya-posle-remonta/
и откройте полный список профессиональных хитростей!
Ваш дом заслуживает сиять!
Уборка после ремонта — это не просто чистка, это превращение хаоса в гармонию. Не торопитесь, используйте правильные инструменты и следуйте проверенным методам. А если задача кажется неподъёмной, подумайте о профессиональной помощи — она может стать вашим спасением. Готовы узнать больше и сделать уборку лёгкой? Перейдите на https://kliningekb.ru/kak-pravilno-splanirovat-i-organizovat-uborku-pomeshheniya-posle-remonta/, чтобы дочитать статью и открыть все секреты идеальной чистоты. Ваш дом ждёт своего звёздного часа!
Phishing is a form of cybercrime that involves deceiving individuals into providing sensitive information such as usernames, passwords, credit card details, and other personal data. This malicious tactic has evolved over the years into a sophisticated method of attack that leverages social engineering and technological advancements to exploit human emotions like fear, curiosity, and trust. As the internet continues to grow, so does the prevalence of phishing attacks, making it imperative for users to understand the nature of this threat, the techniques employed by attackers, and the methods for protection.
The term "phishing" is derived from the word "fishing," implying that cybercriminals are casting a net to catch unsuspecting victims. Typically, phishing involves the use of fraudulent emails or websites designed to appear legitimate, often mimicking well-known organizations such as banks, online services, or social media platforms. These communications usually contain urgent messages that prompt users to click on malicious links, which lead to sites that resemble authentic web pages.
One common type of phishing attack is spear phishing, where attackers target specific individuals or organizations with personalized messages. This approach increases the likelihood of success because the attackers gather information about their victims beforehand, making the content more convincing. For instance, they may reference current projects, GOOGLE DELETE PHISING mutual acquaintances, or legitimate business accounts, creating a false sense of security.
Another variant is whaling, which specifically targets high-profile individuals within organizations, such as executives or senior management. By using highly tailored messages, whaling attacks aim to extract sensitive corporate information or initiate fraudulent wire transfers. Given the potential financial repercussions and reputational damage, whaling poses a significant risk to companies and their stakeholders.
Phishing has also expanded beyond email, with the emergence of SMS phishing (smishing) and voice phishing (vishing). Smishing involves sending fraudulent text messages that prompt users to provide personal information or click on malicious links. Vishing, on the other hand, is executed through phone calls that impersonate legitimate entities, such as banks or government agencies. These methods leverage technology to reach individuals directly, increasing the persuasion factor in the communication.
The impact of phishing attacks can be severe. Victims may suffer financial losses, identity theft, and unauthorized transactions, while companies can face legal repercussions, loss of customer trust, and data breaches that compromise sensitive corporate information. According to the Anti-Phishing Working Group (APWG), phishing attacks have increased dramatically, with millions of phishing websites reported each year. This growth indicates a pressing need for effective countermeasures.
To combat phishing, it is essential for individuals and organizations to implement robust security practices. One of the first steps is to educate users about the risks associated with phishing and how to recognize potential threats. This education includes training programs that cover the common signs of phishing attempts, such as misspelled URLs, generic greetings, and suspicious attachments.
Another critical measure is the adoption of multi-factor authentication (MFA). MFA provides an additional layer of security by requiring users to confirm their identity through multiple means—such as a password followed by a unique code sent to their mobile device—making it more challenging for cybercriminals to gain unauthorized access.
Regularly updating software and security systems is also crucial. Organizations should ensure that all applications, operating systems, and anti-virus software are kept up to date to protect against known vulnerabilities exploited by attackers. Moreover, utilizing advanced email filtering solutions can help detect and block phishing attempts before they reach the user's inbox.
For individuals, verifying the authenticity of communications is vital. Users should take the time to hover over links to inspect their URLs before clicking, avoid providing personal information in response to unsolicited requests, and be vigilant about any correspondence that evokes a sense of urgency or fear. When in doubt, contacting the organization directly using official contact methods can help confirm the legitimacy of the communication.
In conclusion, phishing is a pervasive cyber threat that can lead to significant financial and personal losses if left unchecked. As technology continues to evolve, so do the tactics employed by cybercriminals. Therefore, understanding the nature of phishing, recognizing its various forms, and implementing effective security measures are essential in protecting oneself and one’s organization from this growing threat. Through education and vigilance, individuals and companies can significantly mitigate the risks associated with phishing and maintain a secure online environment.
Through education and vigilance, individuals and companies can significantly mitigate the risks associated with phishing and maintain a secure online environment.
Genelevde "pencere neden açık" krizi nedeniyle bazı evler kapatıldı. Türkiye’de ilk genelevin İstanbul Beyoğlu’nda Sultan Abdülaziz (1830-1876) döneminde kurulmasından bu yana 189 yıl geçmesine rağmen birçok genelev, hâlen bu dönemden kalma tüzükle yönetiliyor. Osmanlı'dan kalan ve pencere açmayı yasaklayan tüzük, Diyarbakır Genelevi'nde krize neden oldu Diyarbakır’da Osmanlı döneminden kalma tüzük ile yönetilen genelevde "pencere neden açık" krizi nedeniyle bazı evler kapatıldı. Genelev işletmecisi ve çalışanları, Ahlak Büro Amirliği ve bazı doktorlar hakkında suç duyurusunda bulundular. Tesisin etrafına 3-4 metrelik duvarlar örülmüş. İçeriden dışarıyı görmek pek mümkün değil. Burada çalışan hayat kadınları, demir parmaklıkların ardında müşteri bekliyor. Fotoğraf: Independent Türkçe Kadınlar gelen müşterilerle ilk görüşmeyi pencereden yapıyor ve pazarlığın ardından içeri geçiliyor. Bu durumun yaşandığı örneklerden biri de Diyarbakır… "Pencereden görüşülmesi yasak" denilerek verilen ağır cezalar 1991 yılında açılan Diyarbakır Genelevi (Beyaz Evler) kentin 5 kilometre dışında. Diyarbakır Emniyet Müdürlüğüne bağlı Ahlak Polisleri, Osmanlı döneminden kalan tüzük maddelerini dikkate alarak, hayat kadınlarının pencereden görüşmesini yasakladı, ağır cezalar getirdi. Bazı genelevlerin yüzyıldan fazla önce çarşı içerisinde kalması nedeniyle kapı ve pencerelerin kapalı tutulmasını şart koşan tüzük, günümüze uyarlanmayınca ilginç uygulamalarla karşı karşıya kalınıyor.
Diyarbakır Bayanlar Dating Duyuruları Telefon Numaraları. Diyarbakır Dul Hanım Kız Arama Cep Telefonu Numaraları Bulma ve Sohbet İlan Siteleri 2024. Diyarbakır da evlenmek isteyen dul hanımlar, If you have any inquiries pertaining to where by and how to use diyarbakıR esc, you can get in touch with us at our own web site. Diyarbakır da evlenmeyi düşünen 30-40 yaş arası emekli dul kadınlar, 50 yaş ve üzeri olgun ve yaşlı dul hanımlar Diyarbakır da evlenmek için WhatsApp evlilik grupları ve cep telefonu numaraları, Diyarbakır dan Kürt evlilik. Diyarbakır Dul Hanım Bir Arkadaş Arıyorum, Diyarbakır Dul Kadınım Bu şehir diğer şehirler gibi değil size buradan bahsetmeme gerek yok sanırım. Ayrıca sadece Diyarbakır dan değil, dilerseniz diğer doğu illerimizden de. Böyle bir durumda hayal kırıklığı yaşamamanız için en son dul eş duyurularını sizlerle paylaşıyoruz. Web sitemizin amacı, sizi sanal ortamın gülünç risklerinden uzak tutarak sizi tamamen gerçek resim ve fotoğraf profillerine sahip bir platformda buluşturmak ve aynı zamanda eğlenceli vakit geçirmek ve sohbet etmek, ücretsiz mesaj vermektir. Diyarbakır Dul Bayanlar Cep Telefon ve Whatsapp Numaraları. Herkes onun bir insan ailesi için bir yuva olmasını ister.
Merhaba sevgili Diyarbakır Escort Genelev Kadını beyler eğer şehrinizde yüksek sınıf dürüst. En önemlisi, hayatımda mutluluğu ve biraz macerayı önemsiyorum. Bu işi yapıyor olmamın en büyük sebeplerinden bir tanesi de işte budur. Çift olarak görüşmek isteyen karı koca veya sevgililere üçüncü partner eşlik etmede dahil olmak üzere son derece geniş yelpazede bir aralığı sunuyorum. Çerkezköy Escort Sınırsız Ucuz Kızlar buluşurken anın tadını benimle çıkartacaksın. O sizin için doğru kişi olduğumdan kesin emin olabilirsiniz. Dünyadaki en güzel şeyin tadını çıkartmak. Doğal, şehvetli, kaliteli bir geçirmek isteyen azgın beyleri bekliyorum. Ben her erkeğime odaklanır onu mutlu etmek için elimden geleni yapar ve daime ne istediğimi bilirim. Aslında, dürüst, sevecen, romantik, sadık, akıllı, tutkulu, sevgi dolu ve kendine güvenen muhteşem bir olduğumu rahatlıkla söyleyebilirim. Eğer mükemmel volkanik orgazm anları hayal ediyorsanız. İsteyen Diyarbakır Genç Ucuz Escort ve bunun için kadınlığımı keşfetmeye aday erkeklere ihtiyacım var.. Kadın arayışında iseniz o zaman kendinizi daha fazla aramayla meşgul etmeyin. Çünkü en iyisini şu an da buldunuz. Gece Diyarbakır Genç Ucuz Escort boyunca hazzın doruklarına çıkartabileceğim ve tamamen mest edebileceğim.
Her çiftin kendine özgü çok farklı dinamikleri söz konusudur. Herkes üzerine düşeni yapmalıdır. Sorun çiftin ortak sorunu olduğuna göre beraberce çözmeleri gerekir. "Ahmet Bey ile Fatma hanımın ortak deneyimledikleri bir cinsel uyum sorunları" vardır. Hastalığa veya problemlere tek bir tanı koymaktan çok, genel cinsel sorunlar özelinde çiftin tüm sistemi düzeltici modeller sunmalısınız. Olayı biz bu şekilde adlandırmayız. Sorunun o çifte özgü özel bir sorun olduğunu bilmeniz, yine o çifte özel çözüm yolları bulmanızı gerektirir. Bu çok daha kapsayıcı bir adlandırmadır ve alt metinlerde sayısız olumlu güzel mesaj içerir. Tanılar kişileri tedavi etmez, soruna bakış açınızı daraltır ve sizi kısıtlar. Hani tıpta denir ya "hastalık yoktur hasta vardır diye" Burada tam da öyle. Örnek verecek olursak; bizim için "Ahmet beyin sertleşme sorunu" ya da "Fatma hanımın orgazm sorunu" diye bir şey söz konusu olamaz. Mantıklı olan sağlıklı olan budur. Ortak sorun ortak sorumluluk bilinci ve çiftin birlikte irade göstermesi çözüm için müthiş bir fırsat yaratır.
Phishing attacks have become one of the most prevalent threats on the internet today, compromising sensitive information and personal data of millions of users. In an era where digital transactions and online interactions are commonplace, having a reliable security tool is crucial for safeguarding users against such malicious activities. Avast Online Security is one such tool that plays an essential role in protecting users against phishing attempts. In this article, we will explore how Avast identifies and blocks phishing sites, the implications of such protective measures for users, and best practices for maintaining online security.
What is Phishing?
Phishing is a cybercrime in which attackers impersonate a legitimate organization or individual to trick victims into providing sensitive information, such as usernames, passwords, credit card details, or personal identification numbers. This is often done through deceptive emails, websites, or text messages that appear authentic. Phishing can take various forms, including email phishing, spear phishing (targeted attacks), and GOOGLE DELETE PHISING vishing (voice phishing). Each method relies on manipulating human psychology to elicit trust and persuade individuals to share confidential information.
Role of Avast Online Security
Avast Online Security is a powerful browser extension that enhances users’ online safety by providing real-time protection against various online threats, including phishing. When users navigate the internet, Avast employs advanced algorithms and a constantly updated database of known phishing sites to determine the safety of the pages being visited.
How Avast Detects and Blocks Phishing Sites
- Database of Known Threats: Avast maintains a comprehensive database of websites known for phishing activities. This database is continuously updated based on data aggregated from millions of users and threat intelligence sources. When a user attempts to visit a site, Avast cross-references it against this database to identify potential threats.
Implications of Blocking Phishing Sites
The ability of Avast Online Security to block phishing sites has significant implications for users. First and foremost, it helps prevent identity theft and the unauthorized use of personal information. In a digital landscape where personal data is often the currency of social interactions and transactions, protecting this data is paramount.
Moreover, Avast’s phishing protection promotes a safer browsing experience. By providing real-time alerts and blocking malicious websites, users can explore the internet with greater confidence, knowing there is a layer of security in place. This peace of mind allows individuals to engage in online shopping, banking, and communication without fear of falling victim to scams.
Best Practices for Online Security
While tools like Avast Online Security are instrumental in protecting against phishing attacks, users should also adopt best practices to enhance their online security. Here are some recommendations:
- Stay Informed: Familiarize yourself with the latest phishing tactics and scams. Cybercriminals constantly evolve their methods, and awareness is one of the best defenses.
Conclusion
In an age where digital threats are omnipresent, Avast Online Security serves as a reliable ally in the fight against phishing attacks. By blocking harmful sites and providing real-time alerts, it empowers users to maintain their online security effectively. However, users should remain vigilant and adopt a proactive approach to their cybersecurity practices. By combining the protection offered by Avast with sound cybersecurity habits, individuals can navigate the online world safely and confidently.