Site blog
Phishing is a pervasive and alarming form of cybercrime that targets individuals and organizations through deceptive online tactics. It typically involves fraudulent communications designed to trick recipients into revealing sensitive information, such as passwords, credit card numbers, and personal identification details. With the digital landscape expanding, phishing scams have become increasingly sophisticated, necessitating a comprehensive understanding of their mechanics and the strategies for prevention.
What is Phishing?
Phishing is characterized by attempts to acquire sensitive information by masquerading as a trustworthy entity in electronic communications. This deception can occur through various channels including emails, social media, and text messages, commonly referred to as "smishing" when it occurs via SMS. Phishing campaigns often employ psychological manipulation; attackers create a sense of urgency or curiosity to compel victims into taking hasty actions.
Common Techniques
- Email Phishing: The most prevalent form involves sending fraudulent emails that appear to be from legitimate organizations, such as banks or well-known online services. These messages often contain links to imitation websites that closely mimic the real ones, prompting users to enter their credentials.
The Risks of Phishing
The consequences of falling victim to a phishing attack can be severe, resulting in substantial financial loss and reputational damage. Individuals may lose access to their bank accounts, have their identities stolen, or pay ransoms for hijacked devices. Organizations face risks that can extend beyond financial losses, including data breaches, legal repercussions, and the erosion of customer trust.
Additionally, the psychological impact on victims can be profound, leading to feelings of vulnerability and helplessness. In some cases, the repercussions of a phishing attack extend into broader societal implications, creating a growing need for enhanced cybersecurity awareness and practices.
Prevention Strategies
Effective prevention against phishing requires a combination of awareness, technology, and best practices. Here are key strategies:
- Education and Awareness: Organizations should conduct regular training sessions to educate employees about the signs of phishing attempts and safe online practices. Encouraging a culture of vigilance can help mitigate risks.
Conclusion
Phishing is an ongoing threat in our increasingly digitalized world, evolving in complexity and scale. By understanding the tactics employed by cybercriminals and implementing robust preventative strategies, individuals and organizations can significantly reduce their risk of becoming victims. Continual education, vigilance, and proactive measures are key to battling this pervasive cyber threat. As technology continues to advance, a collective effort to raise awareness and enhance cybersecurity practices will paves the way for a safer online environment for everyone.
Now advise what is really a dangerous toy and what makes a good vibrator. There are a few places/means to get toys. You can buy them at pet stores or via intenet. This is as well as and correct way to get toys. You could also build quite toys. Are generally referred to as DIY (Do-It-Yourself) trend toys. This is the cheapest way to get toys. Finally, you has the potential a involving buying, building, and recycling which for most people is a cheerful medium.
The best feature in this particular site will be the there is only 1 list, "The Top 10 Toys for 2013," on this web site. So if you are pressed for time, just read this Top 10 List for ideas and will also be good glimpse.
You may have learned that you ought to a Associated with toys retain a parrot entertained in order to have a parrot or several avian species. If you're thinking about getting a parrot then get for you to hire a staff of Santa's Elves because you're for you to need these kind of. Most parrots love to eliminate toys. Is just a healthy, necessary, and required actions. After food, water, in addition as your attention, toys are possibly the next most important things within your parrot's country. Toys are not an optional accessory for you parrot; they are essential. Toys provide mental stimulation, physical stimulation, whilst your parrot's beak attached.
Baby's First Golf Club - A superbly unique golf club that is elegant and charming. Locate a personalized version where the golf club length is second step . the club and the club head has your son or daughter's name and birth date inscribed. Club is often made with fiberglass. Need to great for golf lovers and sports lovers.
The action is to start by gathering them upwards. Put in groups of stuffed dog 【MEE】HANGYODON Cozy Beach Toy Fan, nylon/rubber and stuffable toys. Next, inspect 1 for ailments. For example, rips, tears, loose parts etc. Content articles find any, dispose of those.
It also comes by using a parent tray with two cup holders and there's a storage tray or compartment within seats. One complaint i trend toys have heard is that the under seat storage container is broken into 2 smaller containers as averse to one big container it's it hard for carrying a large diaper bag.
While you will head for the nearest pool supplies store to buy toys for ones kids to use while swimming, keep notion that just about all swimming pool stuff on your own kids are at ease. Some manufacturers sell stuff without adhering to safety models. A lot of cases of injuries occur in private pools are a result from toys, however is not all turn out due to faulty or cheap children's pool floats or toys. Many cases of these injuries are also due to negligence and carelessness.
Before you choosed buy the product, you have to read presentation. There should be information round the materials were being used. You must pick one say how the toy is made of nontoxic resources. The recommended ages when the toy can be used should even be presented. You must make sure your kids are of re-decorating . age for that toy trend toys which you are going to buy for it. Different governments will have different regulations in terms of the things that you should written on the product packing and shipping. To make sure that you are buying the right product, need to know only check out reliable traders.
The social got chaotic, but I'm able to see price of the vehicle. Simon preferred to greet all owners and their kids versus playing along puppies. He was petrified of the other dogs but warmed up a little toward the conclusion of the play blind box point in time.
The Internet is a huge way to help you find your favorite types of online pastimes. Simply go to your favorite search engine and enter the types of games you want to play, you are certain to locate them. The Internet is brimming with these free online games and are 1 click outside of the escape on-line games. You will have the to access these great games as part of your convenience. Enable you narrow what kinds of games you enjoy, associated with what epidermis games appreciate most . By doing this you obtains the most from your online experiences and ultimately cure your getting bored.
James Bond Scaletrix put. James Bond is an everlasting popular figure. The gadgets that he has are very famous, a lot famous then Bond by themselves. Now with the Scaletrix you get a even more pleasant as you can do chase down your enemies with this fast automobile. Boys all over will simply love this on the net game.
Baby's First Golf Club - An absolutely unique golf wedge that is elegant and charming. Choose a personalized version where golfing business club length is the capacity of the club and the club head has your child's name and birth date inscribed. Club is often made with fiberglass. Individuals great for golf lovers and sports lovers.
A new trend toys now's for sheer realism. Inside age where simulation games must come as close to reality as possible, Realism is primary to getting the audience, and none can come close to modern free war games waged with airsoft indicators. Airsoft guns would be evolution belonging to the classic BB guns with the early nineteen-eighties. They were originally created in Japan the particular 1980's the Gun control laws your past country prohibiting the regarding actual guns. These guns was a hit and indulged companies to want even more realism. Eventually the spring mechanics of BB guns were replaced with pressurized gas to provides it a more accurate aim. Eventually this was also upgraded into the first electric airsoft guns.
Understanding Replacement Fob Keys: A Comprehensive Guide
In today's world, keyless entry systems have actually become standard in numerous lorries. These systems typically utilize fob keys-- remote gadgets that approve gain access to and control of a vehicle without the requirement for conventional metal keys. Nevertheless, like any electronic gadget, fob keys can stop working, end up being lost, or be harmed. This raises a vital concern for many vehicle owners: what are the alternatives available for changing a fob key? This short article intends to offer an informative summary of fob keys, their replacement choices, expenses, and essential factors to consider.

What is a Fob Key?
A fob key generally serves multiple functions, consisting of:

- Remote Keyless Entry: Allows the owner to unlock or lock the doors from a range.
- Engine Start/Stop: Enables the motorist to start or stop the vehicle's engine without placing a key.
- Alarm Activation/Deactivation: Provides features to set or shut down the vehicle's alarm system.
Table: Common Functions of a Fob Key
| Function | Description |
|---|---|
| remote control car keys replacement Keyless Entry | Unlock/lock doors from a range. |
| Engine Start/Stop | Start or turn off the engine with the push of a button. |
| Alarm Activation | Activate/deactivate the vehicle's alarm system. |
| Panic Button | Sounds the vehicle's alarm, hindering potential threats. |
Why Would You Need a Replacement Fob Key?
There are several situations in which a vehicle owner might need a replacement fob key:
- Loss or Theft: If the fob key is lost or stolen, it's important to replace it to prevent unauthorized gain access to.
- Damage: Fob keys can experience wear and tear, leading to breakdown.
- Battery Issues: If the fob key's battery is dead, replacing the battery may not constantly restore performance.
Replacement Options for Fob Keys
If you discover yourself requiring a replacement car key remote fob key, there are several paths you can take:
1. Dealership Replacement
One of the most simple-- but frequently expensive-- options is to acquire a replacement from a car dealership.
Pros:
- OEM quality and compatibility.
- Professional shows and assurance.
Cons:
- Higher expenses compared to other options.
- Time-intensive depending upon dealer schedule.
2. Locksmith Services
Mobile locksmiths frequently use fob key replacement services at a more inexpensive rate.
Pros:
- Usually more economical than dealerships.
- 24/7 availability for emergencies.
Cons:
- Quality might differ; ensure the locksmith professional has experience with electronic fobs.
- Might not have access to all required programming tools for specific designs.
3. Third-Party Retailers
Retailers and online markets use replacement fob keys and cut key blades that can typically be configured for your vehicle.
Pros:
- Usually cheaper than automatic car key replacement dealership costs.
- Convenient acquiring from online platforms.
Cons:
- Risk of incompatible items.
- Possibly lengthy shows procedure.
4. DIY Programming
In many cases, vehicle owners can buy blank fob keys and program them themselves.
Pros:
- Economical choice if you have the necessary tools and directions.
- Control over the whole procedure.
Cons:
- Requires understanding of your vehicle's particular programs treatments.
- Risk of faulty programming if guidelines are not followed correctly.
Table: Cost Comparison of Fob Key Replacement Options
| Replacement Option | Estimated Cost | Programming Included? |
|---|---|---|
| Dealer | ₤ 150 - ₤ 400 | Yes |
| Locksmith | ₤ 50 - ₤ 250 | May vary |
| Third-Party Retailers | ₤ 30 - ₤ 150 | May vary |
| how Do You Get a replacement Car key IT YOURSELF | ₤ 20 - ₤ 100 | No |
Often Asked Questions (FAQs)
Q1. How can I tell if my fob key is broken?
- Symptoms of a faulty fob key consist of:
- Unresponsive buttons.
- Indicator lights that do not light up when pressed.
- Difficulty in beginning your vehicle.
Q2. Can I drive my car without a fob key?
In contemporary cars designed for keyless entry, it is often difficult to drive the car key replacement service without a fob key. Some designs may have backup systems, however this differs by make and model.
Q3. Is it possible to sync a replacement fob key with my car?
Yes, a lot of replacement fob keys require specific programs to sync with your vehicle. Consult your owner's handbook or an expert for the exact steps.
Q4. How frequently do fob keys require replacement or battery changes?
Fob key batteries generally last 2-3 years, but this can differ based upon use. If you regularly discover yourself needing to replace batteries or if the key starts acting unpredictably, it may be time to think about a replacement.
In conclusion, the need for a replacement car remote fob key is a regrettable but typical problem for vehicle owners. Comprehending the choices available-- from dealership replacements to DIY services-- can assist in making an informed option that matches both your needs and budget. Ensuring that functionality and compatibility are focused on throughout the replacement process will help maintain the convenience that keyless entry systems provide. Vehicle owners must remember the importance of securing their fob keys to prevent the inconvenience of replacement altogether.
Phishing is a pervasive and alarming form of cybercrime that targets individuals and organizations through deceptive online tactics. It typically involves fraudulent communications designed to trick recipients into revealing sensitive information, such as passwords, credit card numbers, and personal identification details. With the digital landscape expanding, phishing scams have become increasingly sophisticated, necessitating a comprehensive understanding of their mechanics and the strategies for GOOGLE DELETE PHISING prevention.
What is Phishing?
Phishing is characterized by attempts to acquire sensitive information by masquerading as a trustworthy entity in electronic communications. This deception can occur through various channels including emails, social media, and text messages, commonly referred to as "smishing" when it occurs via SMS. Phishing campaigns often employ psychological manipulation; attackers create a sense of urgency or curiosity to compel victims into taking hasty actions.
Common Techniques
- Email Phishing: The most prevalent form involves sending fraudulent emails that appear to be from legitimate organizations, such as banks or well-known online services. These messages often contain links to imitation websites that closely mimic the real ones, prompting users to enter their credentials.
The Risks of Phishing
The consequences of falling victim to a phishing attack can be severe, resulting in substantial financial loss and reputational damage. Individuals may lose access to their bank accounts, have their identities stolen, or pay ransoms for hijacked devices. Organizations face risks that can extend beyond financial losses, including data breaches, legal repercussions, and the erosion of customer trust.
Additionally, the psychological impact on victims can be profound, leading to feelings of vulnerability and helplessness. In some cases, the repercussions of a phishing attack extend into broader societal implications, creating a growing need for enhanced cybersecurity awareness and practices.
Prevention Strategies
Effective prevention against phishing requires a combination of awareness, technology, and best practices. Here are key strategies:
- Education and Awareness: Organizations should conduct regular training sessions to educate employees about the signs of phishing attempts and safe online practices. Encouraging a culture of vigilance can help mitigate risks.
Conclusion
Phishing is an ongoing threat in our increasingly digitalized world, evolving in complexity and scale. By understanding the tactics employed by cybercriminals and implementing robust preventative strategies, individuals and organizations can significantly reduce their risk of becoming victims. Continual education, vigilance, and proactive measures are key to battling this pervasive cyber threat. As technology continues to advance, a collective effort to raise awareness and enhance cybersecurity practices will paves the way for a safer online environment for everyone.
# Harvard University: A Legacy of Excellence and Innovation
## A Brief History of Harvard University
Founded in 1636, **Harvard University** is the oldest and one of the most prestigious higher education institutions in the United States. Located in Cambridge, Massachusetts, Harvard has built a global reputation for academic excellence, groundbreaking research, and influential alumni. From its humble beginnings as a small college established to educate clergy, it has evolved into a world-leading university that shapes the future across various disciplines.
## Harvard’s Impact on Education and Research
Harvard is synonymous with **innovation and intellectual leadership**. The university boasts:
- **12 degree-granting schools**, including the renowned **Harvard Business School**, **Harvard Law School**, and **Harvard Medical School**.
- **A faculty of world-class scholars**, many of whom are Nobel laureates, Pulitzer Prize winners, and pioneers in their fields.
- **Cutting-edge research**, with Harvard leading initiatives in artificial intelligence, public health, climate change, and more.
Harvard’s contribution to research is immense, with billions of dollars allocated to scientific discoveries and technological advancements each year.
## Notable Alumni: The Leaders of Today and Tomorrow
Harvard has produced some of the **most influential figures** in history, spanning politics, business, entertainment, and science. Among them are:
- **Barack Obama & John F. Kennedy** – Former U.S. Presidents
- **Mark Zuckerberg & Bill Gates** – Tech visionaries (though Gates did not graduate)
- **Natalie Portman & Matt Damon** – Hollywood icons
- **Malala Yousafzai** – Nobel Prize-winning activist
The university continues to cultivate future leaders who shape industries and drive global progress.
## Harvard’s Stunning Campus and Iconic Library
Harvard’s campus is a blend of **historical charm and modern innovation**. With over **200 buildings**, it features:
- The **Harvard Yard**, home to the iconic **John Harvard Statue** (and the famous "three lies" legend).
- The **Widener Library**, one of the largest university libraries in the world, housing **over 20 million volumes**.
- State-of-the-art research centers, museums, and performing arts venues.
## Harvard Traditions and Student Life
Harvard offers a **rich student experience**, blending academics with vibrant traditions, including:
- **Housing system:** Students live in one of 12 residential houses, fostering a strong sense of community.
- **Annual Primal Scream:** A unique tradition where students de-stress by running through Harvard Yard before finals!
- **The Harvard-Yale Game:** A historic football rivalry that unites alumni and students.
With over **450 student organizations**, Harvard students engage in a diverse range of extracurricular activities, from entrepreneurship to performing arts.
## Harvard’s Global Influence
Beyond academics, Harvard drives change in **global policy, economics, and technology**. The university’s research impacts healthcare, sustainability, https://www.harvard.edu/ and artificial intelligence, with partnerships across industries worldwide. **Harvard’s endowment**, the largest of any university, allows it to fund scholarships, research, and public initiatives, ensuring a legacy of impact for generations.
## Conclusion
Harvard University is more than just a school—it’s a **symbol of excellence, innovation, and leadership**. Its **centuries-old traditions, groundbreaking discoveries, and transformative education** make it one of the most influential institutions in the world. Whether through its distinguished alumni, pioneering research, or vibrant student life, Harvard continues to shape the future in profound ways.
Would you like to join the ranks of Harvard’s legendary scholars? The journey starts with a dream—and an application!
Bir seks kadını! Evet tam manası ile bir seks kadınıyım ben ama başına gelmemesi gereken bir şey geldi bu kadının! Dul kaldı ama sekslerden de ayrılması anlamına gelmezdi ki bu durum, eğlenmeye dul escort bayan olarak da devam ediyor! Aslında 5 ay önce boşandım, boşanmak isteği benden geldiği için asla üzülmedim, asla da üzülmeyeceğimden emin olabilirsiniz. Sizlerle de zaman geçirirken çok güzel şeyler yapabilirim ama bunun için diyebilirim ki arkadaşlar bu sarışına hak ettiği ödeme de peşin yapılmalıdır. Aksi halde ben içimde bir huzursuzluk oluyor ve 27 yaşındaki esmer bedeni dul escort bayan iken erkeklere de tam manası ile veremiyorum! Bu huzursuzluk asla bende olmamalıdır. Erkeklerim sanırım bana gelmeleri ile ödemelerini yaparak beni bu soğuk durumdan da kurtarırlar ki hemen ben de erkeklerin zaten uzun zaman içlerinde olan soğukluktan kurtulmalarına vesile olacağım, emin olabilirsiniz bu durumdan! Aslında ben erkekleri korunmasız da delirtebilirim ama tabii ki ücretlendirme o zaman fırlar da fırlar.
Özenle tasarlanmış bir web sitesi aracılığı ile hizmet almanın farkını bizimle yaşayabilirsiniz. Fakat belirtmek gerekirse site içerisinde bulunan yalan bilgileri resimlerin değişime uğraması veya iletişime geçtiğiniz bayanlarla yaşayabileceğini sorunlardan sitemiz kesinlikle herhangi bir sorumluluk kabul etmemektedir. En önemli sıkıntıların başında dolandırıcılık gelmektedir. Web sitemiz genellikle gerçek bilgileri yansıtmakta, sahte oluşabilecek bilgilerden uzak durmaktadır.Şirinevler Escort Bu nedenle dolandırıcılığa uğrayan kişilerin bizlere verdiği bilgiler doğrultusunda çözüm üretmeye çalışıyoruz. Fakat bu konuda dikkatli olunmasını tavsiye ederiz. Makyajları, giyim ve hareket tarzları ile normal kadınlardan çok farklı bir arz yaratan Şirinevler Escort bayanlar web sitesi içerisinde tüm iletişim bilgilerini tanıtım bilgilerini sizlere sunmaktadır. Buradan gerekli bilgilere ulaşarak kendinize en uygun hatunu seçebilirsiniz. Onlarla birlikte tatil yapabilir, özel davetlere katılabilir veya gecelik ilişkiler içerisinde eğlence mekanlarına giderek doyasıya eğlenebilirsiniz. Oluşturduğumuz web sitesi bir tanıtım sitesi olup içerisinde yapılabilecek değişimler ve kopyalama işlemlerinde kesinlikle sorumluluk kabul edilmemektedir.Şirirnevler Escort Bu nedenle gerçek bilgileri aldığınızdan emin olmak için karşınızdaki bayanla görüntülü görüşme yapmadan ödeme yapmamanızı tavsiye ederiz. Web sitemizi kullanarak mutluluğu yakaladığında esas bizler de ayrıca mutlu olacağımızı belirtmek isteriz.
İlk cinsel ilişkide kan gelmemesi kadının bakire olmadığını mı gösterir? Kızlık zarı vajina girişinden 1,5 cm içeride doğuştan delik olan esnek bir yapıdır ve ilk cinsel ilişkide kızlık zarında hafif bir açılma olur. Aslında kanama olmaması normalde beklenen bir durumdur. Normal şartlar altında, normal bir kızlık zarı, ister ilk gece olsun isterse yüzüncü gece, kanamaz, delinmez, patlamaz ya da yırtılmaz. Kadın rahat ve kendini kasmazsa, sulanması olmuşsa, penis girişini hissetmez. Kızlık zarının açılması denilen olgu giyilen ince çorabın bir yere takılıp kaçması gibidir. Ayrıca penisin vajinaya girmesiyle ilk açılma sırasında kızlık zarından gelen kan, parmağın kanaması gibi değildir, belli belirsiz bir sıvıdır. Bu da kadın rahatsa, kendini kasmazsa, sulanması tam olmuşsa fark edilmez bile… Kadınlardaki G noktası tam olarak nerede bulunur? 1940’larda Alman jinekolog tarafından adı konulan G noktasının, kadının en erojen bölgelerinden biri olduğu söylenmektedir. G noktasının vajina duvarında, yaklaşık 5 cm derinlikte bulunan bir alandır. Bu bölgenin, kadının orgazma ulaşmasını kolaylaştırdığı söylenmektedir.
Gerçekten nasıl bir Büyükçekmece Escort kadın istediğini biliyorsan o zaman sitemiz içinde herkese hitap eden muhakkak en az bir kadın olduğundan ki eminiz. Biz bu konuda en az 1 bir derken de çok mütevazı davrandık! Sizler sitemizde istediğinizi bulacak, istediğiniz o özel İstanbul Escort ile zaman geçirebileceksiniz ama şu da var kararsınız? O zaman sizlere maalesef kimse yardımcı olamaz! İstediğiniz en absürt şeyi bildirin bile, kategorilerimizi inceleyin mesela istiyorsanız yabancı bir kadın bu kategorilere göz artık, resimleri inceleyin hatta eğer istediğiniz Avrupa Yakası Moldovyalı Büyükçekmece Escort ise o zaman da bu kategoride gezinin, Diyarbakır escort eminiz biz sizlerin istediğiniz kadına ulaşması zaman almayacak. Çünkü bu Moldovyalı Avrupa Yakası Escort Bayanlar aynı zamanda sadece kendilerinden yazıları ile sitemizde bahsetmiyor. Bir de resimleri ile güzelliklerini de sizlerin gözlerinin önüne seriyorlar. E bu da kısa zamanda aşka neden oluyor. Sitemizin aşka neden olduğunu da hemen anlayacaksınız! E biz de bunun için çabalıyoruz. Büyükçekmece ve Mimaroba gibi semtlerde de eskort kızlar yer alır. Kendi evinde görüşenleri bulabileceğiniz gibi Eve Otele gelen escort kızları da bulabilirsiniz. İsteyenler için ; beylikdüzü escort - silivri escort - bahçeşehir escort kızlarının sayfalarını da gezebilirsiniz.
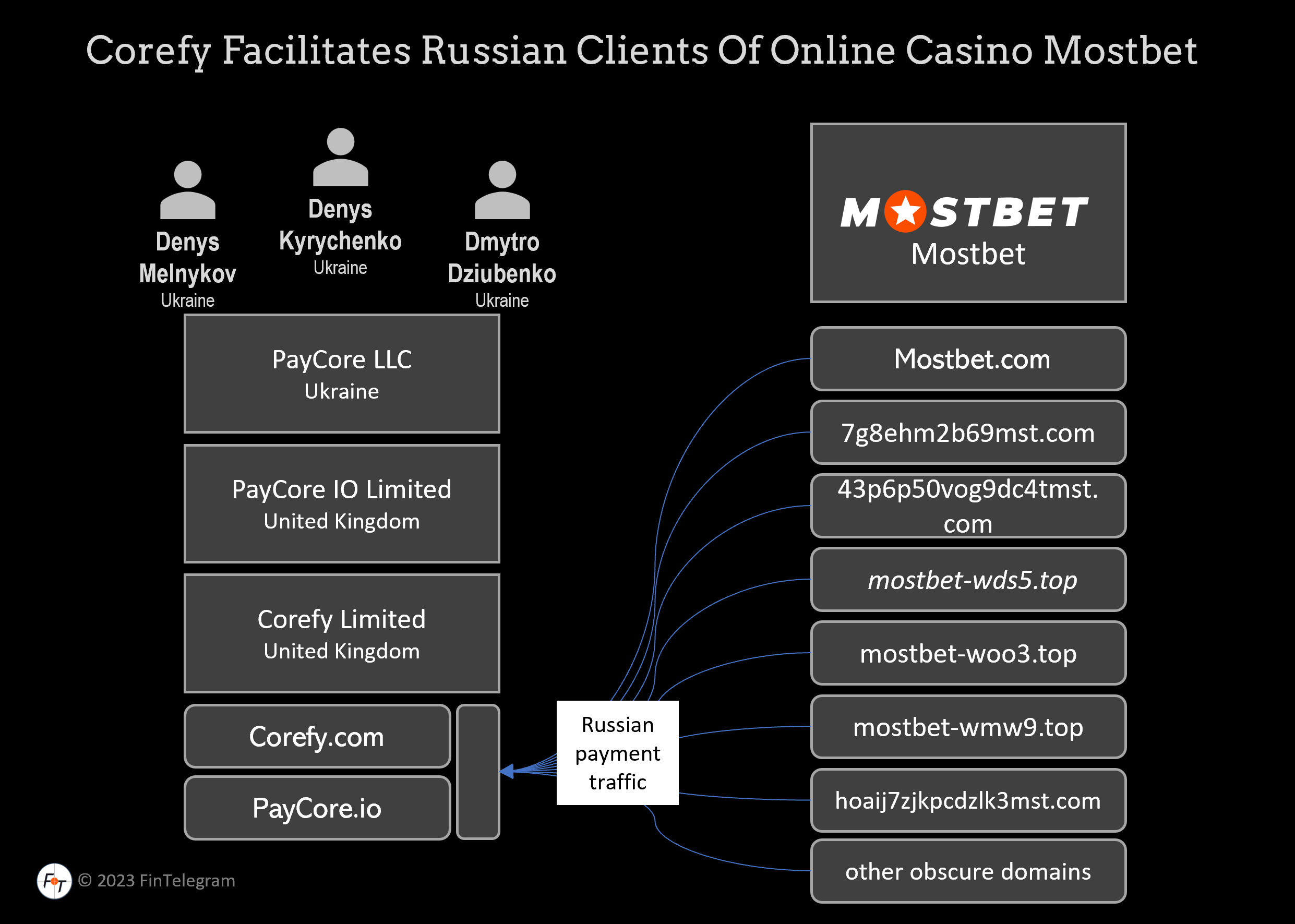
Mostbet: The Premier Betting Destination
As a leading name in digital entertainment, Mostbet stands tall as a trusted brand mostbet uz that delivers unparalleled betting experiences. Operating globally since 2009, mostbet играть we've mastered the science of blending thrilling gameplay with cutting-edge technology.
Our Competitive Edge
Extensive selection of casino games including over 50 sports disciplinesIndustry-leading odds to boost your earning potentialSwift transactions with 40+ banking optionsLucrative reward system valued at €500 for new players24/7 player assistance in 10+ languagesWant to join the winners' circle? mostbet 2025 now!
Our Gaming Portfolio
At Mostbet, every player finds their ideal game:
Sports Betting Section
Covering major leagues to niche sports, our sportsbook showcases 1000+ weekly matches with live streaming and mostbet Венгрия partial withdrawal options.
Real-Time Gaming
Immerse yourself our luxurious live casino with professional dealers hosting blackjack rounds in HD resolution.
Virtual Games
Try our innovative eSports selection with life-like simulations and regular events.
Mobile Gaming Revolution
Our Mostbet application delivers seamless betting anytime, mostbet anywhere:
User-friendly interface optimized for mostbet Ukraine mobile devicesExclusive mobile bonuses inaccessible on desktopOne-tap access to every service even live streamingBiometric login options for secure accessDownload now and mostbet зеркало carry the thrill in your pocket! mostbet
Security & Fair Play
Player security is our focus:
Regulated by Curacao eGaming256-bit protection for all transactionsProvably fair systems for fair outcomesPlayer protection tools such as self-exclusionJoin a community of millions of satisfied players worldwide! mostbet зеркало
 Phishing is a pervasive and alarming form of cybercrime that targets individuals and organizations through deceptive online tactics. It typically involves fraudulent communications designed to trick recipients into revealing sensitive information, GOOGLE DELETE PHISING such as passwords, credit card numbers, and personal identification details. With the digital landscape expanding, phishing scams have become increasingly sophisticated, necessitating a comprehensive understanding of their mechanics and the strategies for prevention.
Phishing is a pervasive and alarming form of cybercrime that targets individuals and organizations through deceptive online tactics. It typically involves fraudulent communications designed to trick recipients into revealing sensitive information, GOOGLE DELETE PHISING such as passwords, credit card numbers, and personal identification details. With the digital landscape expanding, phishing scams have become increasingly sophisticated, necessitating a comprehensive understanding of their mechanics and the strategies for prevention.
What is Phishing?
Phishing is characterized by attempts to acquire sensitive information by masquerading as a trustworthy entity in electronic communications. This deception can occur through various channels including emails, social media, and text messages, commonly referred to as "smishing" when it occurs via SMS. Phishing campaigns often employ psychological manipulation; attackers create a sense of urgency or curiosity to compel victims into taking hasty actions.
Common Techniques
- Email Phishing: The most prevalent form involves sending fraudulent emails that appear to be from legitimate organizations, such as banks or well-known online services. These messages often contain links to imitation websites that closely mimic the real ones, prompting users to enter their credentials.
The Risks of Phishing
The consequences of falling victim to a phishing attack can be severe, resulting in substantial financial loss and reputational damage. Individuals may lose access to their bank accounts, have their identities stolen, or pay ransoms for hijacked devices. Organizations face risks that can extend beyond financial losses, including data breaches, legal repercussions, and the erosion of customer trust.
Additionally, the psychological impact on victims can be profound, leading to feelings of vulnerability and helplessness. In some cases, the repercussions of a phishing attack extend into broader societal implications, creating a growing need for enhanced cybersecurity awareness and practices.
Prevention Strategies
Effective prevention against phishing requires a combination of awareness, technology, and best practices. Here are key strategies:
- Education and Awareness: Organizations should conduct regular training sessions to educate employees about the signs of phishing attempts and safe online practices. Encouraging a culture of vigilance can help mitigate risks.
Conclusion
Phishing is an ongoing threat in our increasingly digitalized world, evolving in complexity and scale. By understanding the tactics employed by cybercriminals and implementing robust preventative strategies, individuals and organizations can significantly reduce their risk of becoming victims. Continual education, vigilance, and proactive measures are key to battling this pervasive cyber threat. As technology continues to advance, a collective effort to raise awareness and enhance cybersecurity practices will paves the way for a safer online environment for everyone.
Phishing is a form of cybercrime that involves tricking individuals into revealing sensitive information, such as usernames, passwords, credit card details, or other personal data. This is generally done through deceptive emails, fake websites, or instant messages. As the internet continues to evolve and become a crucial aspect of daily life, online phishing schemes are becoming increasingly sophisticated, posing significant risks to individuals and organizations alike. Understanding the mechanisms behind these threats is essential for enhancing online security and preventing fraud.
The Mechanics of Phishing
Phishing attacks typically employ social engineering techniques to manipulate users into giving up their information. Attackers often impersonate legitimate entities, such as banks, e-commerce sites, or even colleagues within a workplace. The initial contact usually comes in the form of an email, but phishing can also occur via text messages (known as smishing), phone calls (vishing), or social media platforms.
Upon encountering a phishing attempt, users may receive an email that appears authentic but contains a sense of urgency or threat. For example, the email may claim that there is an issue with their account or that immediate action is required to resolve a security concern. This urgency can pressure users into clicking links that lead to counterfeit websites designed to look identical to the legitimate sites.
Types of Phishing Attacks
- Email Phishing: The most recognized form, where attackers send fraudulent emails mimicking trusted entities. The emails often contain harmful links or attachments that can compromise security.
Risks Associated with Phishing
The ramifications of falling for a phishing scam can be severe. Individuals may experience identity theft, financial loss, and emotional distress. For organizations, phishing can lead to data breaches, loss of sensitive information, financial losses, and damage to reputation. Additionally, the fallout can extend to customers, clients, and other stakeholders who trust the organization that has been compromised.
Furthermore, phishing can lead to ransomware attacks, where hackers lock access to systems and demand ransom for the decryption key. Such attacks can immobilize businesses and lead to lengthy recovery times, costing not just money but creating long-lasting reputational damage.
Signs of Phishing Attempts
Identifying phishing attempts is crucial to preventing them. Common signs include:

- Misspellings or grammatical errors in the email content.
Preventive Measures
Preventing phishing attacks involves a combination of technology, awareness, and best practices. Here are some effective strategies:
- Education and Training: Regularly educating employees and individuals about phishing tactics can improve awareness and response to suspicious emails or messages.
Conclusion
Phishing remains a pervasive threat in the digital age, exploiting human vulnerabilities and advancing technologies. As attackers devise new strategies, it is vital for individuals and organizations to stay informed about the latest phishing tactics and implement robust preventative measures to safeguard sensitive information. Awareness and education play critical roles in combating phishing and ensuring a more secure online environment for everyone. Only through proactive engagement can we hope to minimize the risks posed by these malicious attacks and protect our digital identities.
Phishing is a type of online fraud that seeks to compromise sensitive information from unsuspecting individuals, primarily through the creation of counterfeit websites that mimic legitimate services. This article discusses the technical and ethical considerations surrounding the creation of phishing sites for online banking, emphasizing that no such activity should be undertaken.
Understanding Phishing
Phishing attacks are typically carried out by cybercriminals who create fraudulent websites that appear to be legitimate banking sites. These sites often use closely related domain names, visually similar layouts, and identical login forms. Their objective is to deceive users into entering their credentials, which are then harvested for malicious purposes.
The Technology Behind Phishing Sites
Phishing sites rely on various technologies that enable them to mimic legitimate banking platforms convincingly. Below are some of the common tools and techniques employed:
- Domain Spoofing: Cybercriminals often purchase domain names that closely resemble the target website. For instance, a phishing site could use "bankname-secure.com" instead of "bankname.com". Variations can include adding characters, replacing letters with similar ones, or altering subdomains.
The Process of Creating a Phishing Site
While the technological components of phishing can be explained in a straightforward manner, detailing the step-by-step process of creating a phishing site would be irresponsible and unethical. It is crucial to note that engaging in such activities is illegal in many jurisdictions and can result in severe penalties, including imprisonment.
The Ethical Implications
Engaging in the creation and implementation of phishing schemes is not merely a technical endeavor; it reflects a significant ethical breach. The act of deceiving individuals for financial gain runs contrary to principles of integrity and respect for others. Moreover, GOOGLE DELETE PHISING the consequences of phishing extend beyond financial loss; they can lead to identity theft, emotional distress, and a loss of trust in online systems.
Prevention and Awareness
Given the prevalence of phishing attacks, it is essential to invest in awareness and education for the public. Banks and institutions should implement comprehensive educational programs to help users identify phishing attempts. Customers should be made aware of the following practices:
- Verifying URLs: Always check the URL of the site before entering personal details. Legitimate banking sites will have correct domain names and secure HTTPS connections.
Conclusion
Creating phishing sites for online banking represents a grave violation of ethical standards and legal frameworks. It serves as an alarming reminder of the vulnerabilities present in online systems. Understanding the technologies behind such attacks can foster better defensive strategies and promote awareness among the general public. It is imperative to focus on secure online practices and the promotion of cybersecurity, working collectively to protect users from the devastating effects of phishing.