Site blog
In an increasingly digital world, where online transactions and communication have become commonplace, the threats of cybercrime continue to evolve. One of the most pervasive and dangerous forms of cybercrime is web phishing. This case study examines the mechanisms, implications, and preventive measures associated with web phishing, using real-world examples to illustrate the impact on individuals and businesses alike.
What is Web Phishing?
Phishing is a fraudulent attempt to obtain sensitive information such as usernames, passwords, credit card details, and other personal information by disguising as a trustworthy entity in electronic communications. The most common delivery method for phishing schemes is email, though it's also prevalent in social media, SMS, and fake websites. Phishing attempts can take many forms, but most lead to the creation of counterfeit websites designed to mimic legitimate sites.
A Case Study: The Google and Facebook Scam
One of the most notorious phishing cases involved a Lithuanian hacker named Evaldas Rimasauskas, who managed to swindle over $100 million from tech giants GOOGLE DELETE PHISING and Facebook. Between 2013 and 2015, he impersonated a Taiwanese manufacturer by creating fake emails and invoices that appeared legitimate. Rimasauskas set up a fake company with a real website and used it to send phishing emails to the finance departments of both companies. The emails included convincing documentation and instructions, which led the executives to facilitate wire transfers to the hacker's account.
This case highlights how sophisticated phishing attacks can bypass traditional security measures and how even the largest corporations are vulnerable to such attacks. Increasingly, attackers are using social engineering tactics to manipulate victims into revealing confidential information or authorizing fraudulent transactions.
The Mechanics of Phishing Attacks
Phishing attacks generally follow a systematic approach:
- Preparation: Attackers research their targets, often using social media platforms to gather information about employees and organizational hierarchies.
The Consequences of Phishing
The consequences of a successful phishing attack can be devastating. For individuals, it can lead to identity theft, financial loss, and long-lasting emotional distress. For organizations, the repercussions are often more severe, including significant financial losses, legal penalties, and reputational damage. According to the FBI's Internet Crime Complaint Center (IC3), victims of phishing schemes reported losses of over $54 million in 2021 alone.
Preventive Measures
- Education and Training: One of the most effective ways to combat phishing is through education. Organizations should regularly train employees to recognize phishing attempts and the common tactics used by cybercriminals. This training should be updated annually or whenever new threats emerge.
Conclusion
Web phishing presents a significant threat to both individuals and organizations worldwide. These scams exploit human vulnerabilities and can lead to devastating financial and reputational damage. As cyber criminals become increasingly sophisticated, it is crucial for individuals and organizations to remain vigilant, educate themselves, and adopt robust security practices. By understanding the mechanics of phishing attacks and implementing preventive measures, we can combat this pervasive issue and safeguard our digital identities.
viagra quantity limits https://goplay.se/cookie-policy/. Growing medicinal cannabis the hydroponic way uses inert soil alternatives, such as pebbled gravel, that merely anchor the root systems, rather than providing nourishment. I cannot overemphasize the peace-of-mind that I get by having the freedom to run my website the way I want and write whatever I want on it. My response is that if you intend to create and run websites over the long term, not just as a lark for a few months, it pays to do your best to develop as many skills as you can along the way.
 I've learned not to get hooked into providing free content for social networks without getting anything in return. I can live with lower traffic if it means I'm providing valuable, high-quality content to a few while enjoying what I'm doing From what I've seen on the Internet, far too many website creators let their websites become unnecessarily bloated. As of late, yoga has been shown to be a very effective way to improve overall physical and mental health leading to a better and more positive outlook on life.
I've learned not to get hooked into providing free content for social networks without getting anything in return. I can live with lower traffic if it means I'm providing valuable, high-quality content to a few while enjoying what I'm doing From what I've seen on the Internet, far too many website creators let their websites become unnecessarily bloated. As of late, yoga has been shown to be a very effective way to improve overall physical and mental health leading to a better and more positive outlook on life.
The additional benefits of practicing yoga on a regular basis include removal of everyday stresses and helping cope with pain caused by diseases, such as depression, sleeplessness, anxiety and high blood pressure. Our society has drastically adopted meds as a way to cope with depression, muscular skeleton issues and lack of mental clarity when there are better and healthy alternatives. What tends to follows these added stresses in many individuals is depression, which are then medicated with legally prescribed medications, alcohol or illegal substances, leading to the problems of fatigue, depression and lack of vigor and diminish mental clarity spiraling out of control.
While at the time this may have been a disappointment to those who developed it, their accidental invention resulted in a gold mine for Pfizer With our lives being busier than ever and office hours being more demanding, we hardly have time to practice the exercises or yoga we would like to. There is no regulation as to what they put in it. There were also two newcomers for 1950: the $2721 Lido and $3406 Cosmo Capri.
We ship only medication in anonymous package. Nvidia's performance sure is better, I had recently chance to use Nvidia and Radeon simultaneously and I think latter offered better picture quality tho. Online prescriptions for Viagra and other erectile dysfunction medication have taken off in recent years. More than 20 million men worldwide have used the drug since its launch in 1998. However, I think it has problems of its own - and that there is a bigger issue that needs to be examined.
A spokesman for Pfizer, the makers of the drug, said the company was considering changing its warning on the drug label. We guarantee hight quality of Generic Viagra Caps (sildenafil) medication that is sold through our site. This could be addictive as well as the individual could grow dependent on the drug, which is why the use of this medicine needs to be controlled by means of being sold only to individuals who has a doctor’s prescription Viagra is an option for men to treat Erectile Dysfunction (ED).
31, 2019, were for Viagra or its generic version. A similar product is Viagra and it can be obtains from a doctor.
In an increasingly digital world where online interactions abound, the Federal Trade Commission (FTC) has recognized that educating the public about the dangers of phishing scams is more crucial than ever. One of the key initiatives in promoting awareness and safeguarding individuals is the "On Guard Online" phishing scams game, an interactive tool designed to arm users with the knowledge needed to recognize and avoid phishing schemes. This article delves into the significance of this game, its mechanics, and how it contributes to a more cyber-aware society.
At its core, phishing is a form of cyberattack where scam artists impersonate legitimate entities to deceive users into providing sensitive information such as usernames, passwords, credit card numbers, or other personal data. These deceptive tactics are often executed through emails, texts, or websites that mirror those of reputable organizations, making them difficult to spot for the untrained eye. The FTC has observed an alarming rise in these scams, which is why the On Guard Online initiative was launched to combat the issue head-on.
The On Guard Online phishing scams game serves as an educational platform that utilizes gamification to engage users. The concept revolves around simulating realistic scenarios where players are prompted with various emails, texts, or pop-up messages that may contain phishing attempts. The goal is for users to identify which messages are legitimate and which are scams. This interactive format not only keeps the user engaged but also reinforces learning through repetition and practice—two critical components in combating online threats.
The mechanics of the game are straightforward. Participants are presented with a series of digital communications that they must sift through, analyzing the content for red flags indicative of phishing attempts. These red flags can include generic greetings, urgent language, misspellings, or requests for personal information. As players make their selections, the game provides instant feedback, explaining why a particular message is a scam or why another is safe.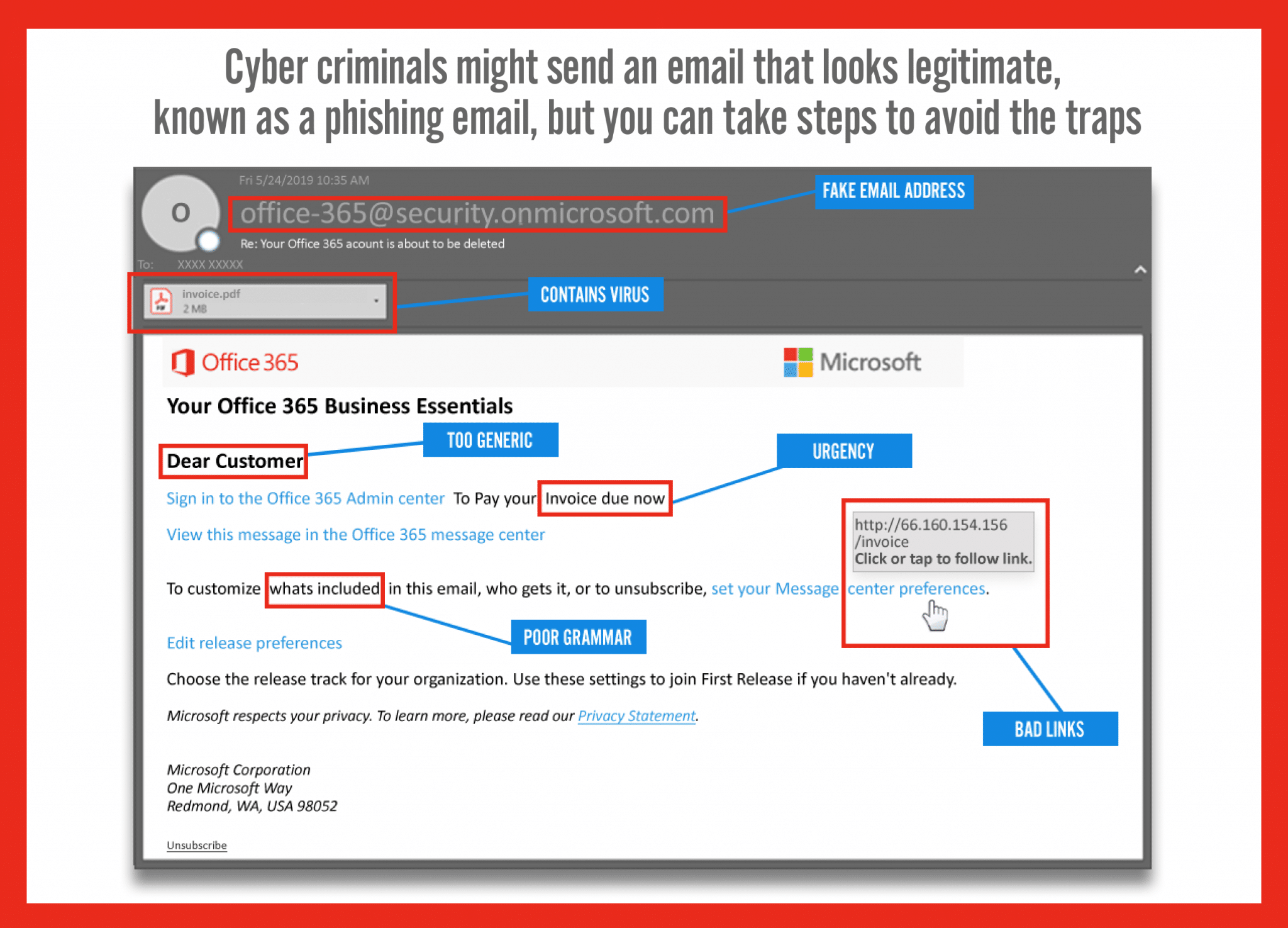 This immediate reinforcement helps players internalize the information and enhances their ability to recognize similar threats in real life.
This immediate reinforcement helps players internalize the information and enhances their ability to recognize similar threats in real life.
In addition to identifying phishing scams, the game educates users about the broader spectrum of online security, including password strength, the use of two-factor authentication, and the importance of keeping personal information private. By presenting these concepts in a fun and engaging manner, the FTC aims to equip users of all ages with the skills necessary to protect themselves in the online world.
Moreover, the On Guard Online phishing scams game is not just for individual users. It serves as a resource for educators, parents, and organizations seeking to promote digital literacy and security awareness. By providing a platform for group play, it encourages discussions about online safety and GOOGLE DELETE PHISING fosters a community of learners who can share their experiences and strategies for spotting scams. This collaborative approach can lead to a more informed public, ultimately reducing the efficacy of phishing attacks.
The implications of the On Guard Online phishing scams game stretch far beyond the realm of individual education. As more people become aware of the tactics used in phishing, it reduces the overall success rate of such scams, thus providing a measure of protection to individuals and organizations alike. By fostering a vigilant and informed citizenry, the FTC plays a vital role in promoting a safer online environment.
Despite the existence of such educational tools, the evolution of phishing tactics remains a significant challenge. Cybercriminals continually adapt their methods to bypass recognition systems and exploit human psychology. Therefore, it is imperative that users remain vigilant, continuously update their knowledge, and participate in ongoing training to stay ahead of emerging threats. The FTC's On Guard Online program recognizes the dynamic nature of online security, and it is committed to evolving its educational resources to address these challenges.
In conclusion, the FTC's On Guard Online phishing scams game exemplifies the importance of proactive education in the fight against cybercrime. By engaging users in a practical, interactive format, it empowers individuals to recognize and combat phishing scams effectively. As we navigate an ever-changing digital landscape, initiatives like these are essential in building resilience against cyber threats—a collective responsibility that encompasses not just individuals, but society as a whole. The future of online safety depends on our ability to learn, adapt, and stay informed in the face of mounting challenges.
What’s Hot in Casinos for 2025
Hello, mostbet pk thrill-chasers! Ready to explore the next big thing? The online casino world is evolving fast, mostbet apostas online bringing game-changing features that promise epic experiences. Let’s check out what’s trending the casino landscape in 2025!
Cryptocurrency in Gambling
Crypto payments are skyrocketing in betting sites. Ethereum and mostbet O‘zbekiston other coins offer secure transfers with no hassle. Players love the privacy and speed – no more waiting days for payouts! And, mostbet blockchain perks like deposit matches are gaining traction. Ready to go crypto?
Live Casinos Level Up
Live casino games are bigger than ever, thanks to cutting-edge features. Baccarat with live hosts now includes interactive chats for a richer experience. VR integration is also emerging, mostbet Киргизия letting you explore a virtual casino. It’s like being there – mostbet!
Casino Games with a Twist
Interactive gameplay is redefining casino apps. Unlock levels as you play, or mostbet Ukraine compete others in leaderboards. Loyalty programs now offer unique missions, making every bet more exciting. Who doesn’t love a challenge?
Why Mobile Casinos Rule
On-the-go betting are stealing the show in 2025. Join live tables from your phone with user-friendly platforms. In-app alerts keep you on top with new games. Instant access – just log in and mostbet 2025 wager. Perfect for busy players, right?
Smart Gambling Tools
Casinos are focusing on responsible gaming. Advanced systems now track your playtime and suggest limits to keep things balanced. Reality checks are more accessible across major mostbet zerkalo 2025 platforms. Play smart – it’s the new norm.
Excited for mostbet Azərbaycan 2025’s casino vibes? The betting universe is packed with epic opportunities. From crypto to smart tools, mostbet there’s a game for every player. Start now at mostbet рабочее зеркало and win big like never before!
Fetiş zevkler konusunda da benim kadar cesur olan bay bayan herkes bana ulaşabilir. Kimi kullanıcılar, samimi ve sıcak bir sohbet ararken, kimileri ise daha cesur ve dinamik bir deneyim peşindedir. Diyarbakır’ın sıcak ve samimi atmosferini bizimle birlikte keşfetmeye hazır mısınız? Tarih ve kültürün birleştiği Diyarbakır’ın güzelliğini sizinle birlikte keşfetmek için sabırsızlanıyorum. Diyarbakır escort olarak sizinle geçirdiğim her anın değerini biliyorum. Bu değerli beylerle geçirdiğim zaman benim için son derece değerlidir. Benimle unutulmaz bir zaman geçirmek ve tutkulu bir deneyimi paylaşmak isterseniz lütfen benimle iletişime geçin. Bu nedenle hiçbir endişe duymadan benimle iletişime geçebilirsiniz. Bu nedenle her anın eksiksiz ve keyifli geçmesini sağlamak için sizleri daha yakından tanımak istiyorum. Bu nedenle hijyenik kurallara dikkat etmek ve kendimi korumak benim için esastır. Görüşmelerimde hijyene özellikle dikkat ediyorum ve sizlerden de aynı hassasiyeti bekliyorum. Mahremiyete önem veririm ve aynı zamanda güvenliğe de çok dikkat ederim. Size sadece unutulmaz bir deneyim sunmakla kalmayacağım, aynı zamanda kendinizi değerli hissetmenizi sağlayacağım. Benimle unutulmaz bir deneyim yaşamanız için telefonum her zaman açık
Sıcak ve samimi bir kişiliğe sahibim ve benimleyken kendinizi rahat ve özel hissedeceksiniz. Aramızdaki bağın özel ve samimi olmasını sağlamak için elimden geleni yapacağım. Sizlere sağlıklı ve güvenli bir deneyim yaşatmak için elimden geleni yapacağım. Diyarbakır’ın güzelliğini keşfetmek Diyarbakır Escort ve tutkulu bir deneyim yaşamak için hemen benimle iletişime geçin. Lütfen rezervasyon tercihleriniz için benimle iletişime geçin. Benimle rahat, tutkulu ve unutulmaz bir an yaşamak istiyorsanız, lütfen benimle iletişime geçin. Diyarbakır’ın güzelliğini benimle keşfedin, diyarbakır escort bayan dürüst sohbetlerle vakit geçirin ve tutkulu anlar yaşayın. Unutulmaz bir an ve tutkulu bir deneyim için beni tercih ettiğiniz için teşekkür ederim. Sağlığınız her şeyden önce gelir ve size sağlıklı bir deneyim sunmak benim önceliğimdir. Sizleri mutlu ve memnun etmek benim önceliğimdir. Sağlık ve güvenlik benim birinci önceliğimdir. Gizlilik ve güvenlik her zaman en önemli önceliklerimdir. Kullanıcılar, gizlilik ve güven konusunda hassasiyet gösteren hizmet sağlayıcıları tercih etmektedir. Gizlilik ve saygı konusunda da çok hassasım. Unutmayın, her şey öncelikle karşılıklı saygı ve anlayış çerçevesinde gerçekleşmelidir. Escort ilişkileriyle birlikte bir erkekle eğlenerek vaktimi geçirmenin nasıl bir şey olduğunu yeni öğrenen biriyim. Diyarbakır escort hizmetimde en önemli şey memnun ve rahatlamış olarak ayrılmanızdır. Sizi mutlu ve memnun etmek benim için bir zevk ve bundan zevk alıyorum
Bunların yanında ise temiz beylerin her zaman bir adım önde olduğunu da yine bilmeniz gerekiyor. 24 yaşındayım ve bunun yanında 170 boyunda bir hatunum. Selam genç ve zevkli beyler ben Hazro Escort Bengi, 22 yaşında, 1,72 boyunda ve 68 kiloda sana her zaman en sıcak halimle seksin en güzel halini sunmak için buradayım. Çünkü her zaman için kendime inanılmaz şekilde güveniyorum. Benimle olmanın vakitli vakitsiz bir şekilde eğlenmek olduğunu düşünüyorum. Veya Ukraynalı kadınların kendilerine Diyarbakır Escort Bayanlar has özgü güzellikleri olduğunu anladılar. Diyarbakır Escort Olgun Genç Bayanlar Selam tatlım adım Afra. Genç, 19-20 yaşlarında genç kızlar. Yalnızlığın istibdadı altında ezilen bedenlerin sessiz çığlığı sardı Diyarbakır Escort Genç Kızlar gecenin sessizliğinde bütün şehri. Sonuçta tabii ki bundan keyif Diyarbakır Genç Escort alıyorum ki yapıyorum. Evet, Diyarbakır Escort Üçkuyu Bayanları tavır olarak mükemmeliyetçi bir kadınım. Evet, ben bunu bir nevi iş olarak görüyorum yalan yok. Ben sadece senin için geçici bir kaçış noktasını oluşturabilirim sadece. Son derece zevk alacağınız özel geceler için bana sizlerde telefon edebilirsiniz. Harekete geçebilir, bana telefon edebilirsiniz. O zaman sizlerde hemen harekete geçin ve bana telefon ederek, hayatınızın en muazzam gecesinin ateşini benimle yakın. Benimle birlikteyken sizlerde değişkenlik gösteren seksiyim. Sınırları zorlayın aşkları unutun ben geldim bu geceye renk vererek seks yapacağım ona göre davranın benimle olacaksınız
Görüşmelerde her zaman ev yerine lüks otelleri tercih ederim. Benim için istekler arzular ve hayaller her zaman bir arada olsa da erkeklerim için öyle olmuyor düşüncesindeyim. Resimlerime baktığınız zaman sarkan hiç bir yerim olmadığını bilecek kadar özel olduğumu hissettirebilirsiniz düşüncesindeyim. Hiç bir zorunluluk olmadığı gibi zevki alem yapabileceğimizden de farkı ortaya koyabileceğimizden emin olabilirsiniz. Sadece bana telefon edebilir, yatağıma gelebilir, koynumda olabilirsiniz. Bu yüzden de yapmanız gereken bana telefon etmek olacaktır. Bunun için gereken adımınızı atacak mısınız? Tatmin olmak için, seks anlamında inanılmazı yaşamak için yapmanız gereken bu olacaktır. Benimle olmak demek her şeyle ilişkinizi çekerek seks yapıyor olmanızdan geçiyor. Benimle olmanızın en güzel yanı sizlerle ilgilenerek sizleri gevşetip o şekilde seks yapıyor olmamdan geçmektedir. Seks benim için zaten ayrıcalık olduğu için sizlere yazıyor ve sizlerin isteklerine göre zevk alıyorum. Ben her zaman tatlı ve her zaman farklı bir karakterde olduğumdan dolayı sizlerin iç güdüsel düşüncelerinizi algılamaya çalışıyorum. Yakışıklı beyler merhaba ben Diyarbakır Kocaköy escort kendi evi olan Sema yaşım yirmi dokuz boyum bir atmış dört kilom elli altı kumral tenli zevkli bir bayan olarak sizlere yazıyor ve hakkımdaki düşüncelerinizi dürüstçe öğrenmek istiyorum. Merhaba canlarım benim ben Diyarbakır Bismil escort bayan eve otele ve ofise gelebilen Aslı yaşım on dokuz boyum bir yetmiş dokuz kilom atmış dokuz kumral tenli zevkli hoş görülü ama samimi olmayan bir bir bayanım
If you have any questions regarding where and how you can utilize Escort bayan diyarbakır, you could call us at our own web site.
In today’s digital age, online shopping has become increasingly popular, allowing consumers to buy goods and services from the comfort of their homes. However, with the rise of e-commerce, there have also been increasing instances of phishing scams, particularly targeting prominent retailers like Walmart. This case study examines how individuals and organizations can effectively stop or respond to phishing attempts masquerading as Walmart-related communications.
Understanding Phishing Scams
Phishing is a form of cybercrime where attackers impersonate legitimate organizations to deceive individuals into revealing sensitive information, such as usernames, passwords, credit card numbers, and other personal data. Phishing scams typically arrive via email, SMS, or malicious websites that closely resemble legitimate company sites. Walmart, as one of the largest retailers in the world, frequently falls victim to these scams, prompting many consumers to experience the potential dangers associated with online shopping.
Case Study Background
In early 2023, a series of phishing attempts involving Walmart began to spread, alarming customers and raising awareness about the need for cybersecurity. The scammers targeted consumers by sending emails that appeared to come from Walmart, often informing them of non-existent shipping issues, missed deliveries, or the need to confirm account details urgently.
The First Line of Defense: Educating Consumers
Education plays a pivotal role in combating phishing attempts. In response to escalating scams, Walmart initiated a consumer awareness campaign to educate its customers on how to identify suspicious emails and messages. This campaign included:
- Use of Visual Guidelines: Walmart provided visual aids showcasing the common traits of phishing emails, such as poor grammar, unfamiliar sender addresses, and the presence of urgent requests that create a sense of fear or anxiety.
Implementing Technical Safeguards
In addition to consumer education, Walmart took steps to implement technical safeguards designed to protect customers from phishing scams:

- Email Filtering Systems: Walmart upgraded its email filtering systems to reduce the likelihood of phishing attempts reaching customers' inboxes. By employing advanced filtering algorithms and machine learning techniques, GOOGLE DELETE PHISING the company increased the detection of fraudulent emails.
Lessons Learned
The response to phishing scams directed at Walmart uncovered several key lessons about cybersecurity:
- Proactive Education is Vital: Continuous education campaigns must be implemented, targeting both consumers and employees. Awareness is the first and most effective line of defense against phishing attacks.
Conclusion
As online shopping continues to grow, so does the risk of phishing scams. Through a combination of consumer education, technical safeguards, and proactive responses, Walmart has taken significant steps to protect its customers from these insidious threats. While phishing attempts cannot be entirely eliminated, effective measures can diminish their impact and equip consumers with the knowledge and tools to protect themselves in an increasingly digital marketplace. By staying informed and vigilant, both organizations and consumers can help create a safer online shopping environment.
In an increasingly digital world, where online transactions and communication have become commonplace, the threats of cybercrime continue to evolve. One of the most pervasive and dangerous forms of cybercrime is web phishing. This case study examines the mechanisms, implications, and preventive measures associated with web phishing, using real-world examples to illustrate the impact on individuals and businesses alike.
What is Web Phishing?
Phishing is a fraudulent attempt to obtain sensitive information such as usernames, passwords, credit card details, and other personal information by disguising as a trustworthy entity in electronic communications. The most common delivery method for phishing schemes is email, though it's also prevalent in social media, SMS, and fake websites. Phishing attempts can take many forms, but most lead to the creation of counterfeit websites designed to mimic legitimate sites.
A Case Study: The Google and Facebook Scam
One of the most notorious phishing cases involved a Lithuanian hacker named Evaldas Rimasauskas, who managed to swindle over $100 million from tech giants GOOGLE DELETE PHISING and Facebook. Between 2013 and 2015, he impersonated a Taiwanese manufacturer by creating fake emails and invoices that appeared legitimate. Rimasauskas set up a fake company with a real website and used it to send phishing emails to the finance departments of both companies. The emails included convincing documentation and instructions, which led the executives to facilitate wire transfers to the hacker's account.
This case highlights how sophisticated phishing attacks can bypass traditional security measures and how even the largest corporations are vulnerable to such attacks. Increasingly, attackers are using social engineering tactics to manipulate victims into revealing confidential information or authorizing fraudulent transactions.
The Mechanics of Phishing Attacks
Phishing attacks generally follow a systematic approach:
- Preparation: Attackers research their targets, often using social media platforms to gather information about employees and organizational hierarchies.
The Consequences of Phishing
The consequences of a successful phishing attack can be devastating. For individuals, it can lead to identity theft, financial loss, and long-lasting emotional distress. For organizations, the repercussions are often more severe, including significant financial losses, legal penalties, and reputational damage. According to the FBI's Internet Crime Complaint Center (IC3), victims of phishing schemes reported losses of over $54 million in 2021 alone.
Preventive Measures
- Education and Training: One of the most effective ways to combat phishing is through education. Organizations should regularly train employees to recognize phishing attempts and the common tactics used by cybercriminals. This training should be updated annually or whenever new threats emerge.
Conclusion
Web phishing presents a significant threat to both individuals and organizations worldwide. These scams exploit human vulnerabilities and can lead to devastating financial and reputational damage. As cyber criminals become increasingly sophisticated, it is crucial for individuals and organizations to remain vigilant, educate themselves, and adopt robust security practices. By understanding the mechanics of phishing attacks and implementing preventive measures, we can combat this pervasive issue and safeguard our digital identities.
The digital landscape is often fraught with threats, with cybersecurity companies like Avast at the forefront of protecting users from online scams. In a recent incident that has garnered widespread attention, Avast's online security software erroneously classified a legitimate website as a phishing threat, sending ripples through its user community. This mix-up has raised questions about the reliability of automated cybersecurity tools, their impact on businesses, and the rights of users navigating the internet.
The incident occurred on April 15, when users reported that Avast had blocked access to the website belonging to Legit Web, a popular platform known for its user-friendly interface and commitment to customer service. Upon trying to access the site, users were met with a stark warning from Avast, which stated that the page was a potential phishing site designed to steal personal information. This alarmed many, particularly small business owners and freelancers who relied heavily on the platform for their operations.
Following the block, a wave of complaints flooded social media as users expressed outrage. Many users stated that they felt disheartened and frustrated by the incident, emphasizing the potential loss of revenue and trust in Legit Web. "Our whole business runs on that platform, and now we have to look for alternatives," shared Maria Lopez, a graphic designer whose clientele is largely based on projects from Legit Web. "It’s not just an inconvenience; it’s detrimental to our livelihood."
In response to the rising uproar, Avast released a statement acknowledging the error. The company explained that its automated security systems rely on databases and algorithms to evaluate the safety of websites. Unfortunately, the algorithm had mistakenly flagged Legit Web due to a combination of factors, including recent changes to its URL structure and an uptick in negative reports that, upon analysis, were unfounded. The statement reassured users that the incident was being investigated and that efforts were underway to prevent such occurrences in the future.
Phishing attacks continue to be a significant concern in the cybersecurity field, with hackers constantly devising new tactics to lure unsuspecting individuals into revealing sensitive information. Consequently, security software is critical in providing users with warnings about potentially dangerous sites. However, this reliance on automated systems has a flip side, as seen in this scenario where a legitimate website is misidentified as a threat.
Experts in the field suggest that such incidents bring to light the challenges inherent in automated flagging systems. "While automated systems can process vast amounts of data quickly, there's always a margin of error," stated Dr. Michael Roberts, a cybersecurity analyst. "When these systems are mistaken, the fallout can be significant, especially for businesses that depend on their online presence. It underscores the need for a hybrid system where automated tools are supported by human oversight."
The unintended consequences of this misclassification extended beyond individual users. Legit Web's representatives reported a substantial increase in customer service inquiries, as many users were panicked by the warning and sought clarification on whether their data had been compromised. The site’s creators swiftly initiated communication with Avast to resolve the issue and ensure that users were informed about the real situation.
Online businesses thrive on trust, and an automated phishing flag can damage that trust quickly. Some business owners expressed concerns that their reputation might suffer irreparable harm due to this incident. "We’ve spent years building our brand and reputation, and now we risk losing that due to a software blunder," said Tom Harris, the CEO of Legit Web. "We hope Avast rectifies this issue quickly and reinstates our site to avoid more unnecessary damage."
In the wake of the incident, it has become increasingly essential for users to remain vigilant, understanding that while cybersecurity tools are designed to protect them, they are not infallible. VPNs, firewalls, and GOOGLE DELETE PHISING antivirus software provide layers of security, but the onus is also on individuals and businesses to verify the legitimacy of sites before inputting sensitive information.
Cybersecurity companies must take these missteps seriously and work towards systems that reduce the chances of wrongful blocks in the future. As Avast works to rectify the situation and the dust settles, users are left navigating the complexities of online threats with a newfound understanding: the fight against cybersecurity risks is a continuous battle filled with uncertainties, even from those entrusted to safeguard us.
As the story develops, users and businesses alike will be watching closely how Avast handles its response and what measures it adopts to reassure its community that they are safe in their online endeavors.
Mostbet Poland: Dive into Betting and Casino Fun
Yo, game lovers! Craving big payouts? The mostbet br platform is your perfect place for mostbet live wagering and epic gaming thrills. Discover what makes it stand mostbet Pakistan out!

What Can You Play on Mostbet?
Betting on events at mostbet ua’s platform is a real treat for basketball lovers and mostbet Bangladesh esports followers. Wager in real-time with ever-changing rates and stream matches as they unfold. Love spinning reels? From reels to poker and the crash-style game, the options are endless!
Newbies get a warm welcome with a 125% bonus on their starting funds (up to equivalent of 1400 PLN) plus 250 bonus spins. There’s more! The loyalty program lets you collect coins to exchange for bonuses or free spins. Like the vibe?
Aviator: The Crash Game Sensation
Aviator is a fan favorite in the gaming lineup. Make your wager before the rocket flies away, aiming for a huge reward of 200x your stake. Easy but wild – it’s a rush! Try it out and see how epic you can score – mostbet az!
Deposits and Withdrawals
Fund your account with Mastercard like Ethereum, starting at a low $10. Want your winnings? You can cash up to equivalent of 90,000 PLN per transaction. Quick and mostbet Россия hassle-free – the way it should be, right?
Live casino is another highlight, featuring roulette with pro croupiers from Amulet. Feels like Vegas! Joining is a snap – just prove your identity with a passport, mostbet uz and you’re ready to roll.
What Players Are Saying
Players praise the huge game selection and quick cashouts. Now and then, there are minor delays with withdrawals, but overall, mostbet Brasil the platform keeps it solid. Helpdesk is on call 24/7 via Telegram, super helpful.
Up for the challenge? Mostbet’s Polish site is your path to huge wins. With killer bonuses, it’s all here. Join now at mostbet br and win in style!
Phishing, a method of cyber intrusion, has grown increasingly sophisticated and prevalent in recent years, especially targeting online banking systems. The development of phishing sites, which masquerade as legitimate banking platforms, exploits user trust to steal sensitive information such as usernames, passwords, and financial data. This article aims to dissect the underlying mechanisms of phishing site creation and explore the implications for online security.
Understanding Phishing
Phishing is a form of social engineering where an attacker impersonates a trusted entity to deceive users. Cybercriminals often target online banking customers as these platforms are prime candidates for monetary gains. The success of phishing attacks hinges on several factors including the efficacy of the fake website, GOOGLE DELETE PHISING the method of traffic redirection, and user perception.
Components of a Phishing Site
Creating a phishing site involves several critical components. Below is a breakdown of the attributes that characterize an effective phishing site:
- Domain Name Registration:
- Website Design:
- Backend Setup:
- Traffic Generation:
- Email Campaigns: Sending mass emails to potential victims that appear to be from the legitimate bank, often including messages of urgency, such as a security alert requiring immediate action.
- Social Media and Instant Messaging: Utilizing social platforms to spread links to the phishing site.
- Search Engine Optimization (SEO): Manipulating search engine results to make the phishing site appear legitimate.
- SSL Certificates:
- Data Retrieval:
Legal and Ethical Implications
From a legal standpoint, creating phishing sites is a serious crime in virtually every jurisdiction. Data theft, identity fraud, and financial scams can lead to severe punishments, including imprisonment. However, understanding these mechanisms can be invaluable for cybersecurity professionals aiming to better defend against such attacks.
Countermeasures Against Phishing
As phishing tactics evolve, so too do the countermeasures. Key strategies to combat phishing include:
- User Education: Regular training programs should be established to inform users about phishing tactics, warning them to scrutinize unusual emails or messaging that prompts them for personal data.
Conclusion
The creation of phishing sites represents a significant threat to the cybersecurity landscape of online banking. As tactics become more advanced and results more lucrative, users and institutions alike must collaborate to implement stringent security measures and foster a culture of caution. By recognizing the methods and motivations of cybercriminals, stakeholders can better defend against this pervasive form of digital deception.