Site blog
E-posta arşiv dosyası tespit edilmiştir. Valla .. komutanım .. Karşı devrimin karanlığını hep birlikte yeneceğiz. Hükümeti türbanla ilgili yasayı geri çekmeye, milletin sesine kulak vermeye çağınyoruz. Haydi Türkiye göster iradeni! Türkiye'nin devrimcileri, Mustafa Kemal'in askerleri Görev vakti gelmiştir. Bağımsızlık ve Atatürk devrimlerine, laikliğe sahip çıkmak için Ankara'da büyük halk hareketinde buluşuyoruz. HABERLER.doc" isimli MSword belgesinin içeriğinde, şüpheli Hayrettin ERTEKİN tarafından Türbanın üniversitelerde serbest bırakılması ile ilgili Yüce Türk milletine hitaben 9 Şubat Çağrısı başlığı ile bir yazı olduğu, "Türkiye'yi haçlı irticadan kurtarmanın zamanı gelmiştir. If you beloved this article and you would like to obtain a lot more facts with regards to diyarbakır escort kindly take a look at our internet site. Kuvayı Milliye'nin işgal altındaki bir ülkede halk tarafından oluşturulmuş direniş örgütleri olduğunu, bu özellikleri ile bir sivil örgütlenme modeli olduğunu, "Kuvayı Milliye"'nin sonradan Ulusal Kurtuluş Savaşı'na katılan herkesi kapsayan bir kavram olarak kullanıldığını belirttikten sonra; "Günümüzde bu tarz düşünülmek istenilirse bu oluşum modern ordunun uzantısı olarak özel kuvvetler komutanlığının organizesinde oluşturulmaktadır." denilmiştir. 137 tane çalışan var ne arayan var, ne soran" "Kalesi alıp dağa gideyim diyorsanız onu da yaptık zamanında" " BAŞKA YAPACAK BİR ŞEY YOK BOMBA MOMBA DERSENİZ ONLARI BIRAKTIM O İŞLERİ O İŞLERDEN ŞEY OLDUM daha ne yapayım yani" dediği, bir süre gazetelerde yazılar yazılarla ilgili konuştukları ve Y Şahsın seni alkışlıyorum, tebrik ediyorum diyerek Onlarda en azından bir şeyin tepkinin ifadesi AMA HAKKATEN BEN ARZU ETTİĞİM TEPKİYİ BULAMIYORUM VE ZAMAN ZAMAN" "12 EYLÜL ÖNCESİ GÜNLERİ ÖZLÜYORUM' dediği, Hayrettin ERTEKİN'in "AH O GÜNLER OLACAK Kİ ŞİMDİ VARYA ŞİMDİ" diyerek gündemi değerlendirip, terör konularından konuştukları tespit edilmiştir. Tape : 1761, 12.12.2007 tarihi, saat:11.16'da Hayrettin ERTEKİN ile W arasındaki telefon görüşmesinde özetle; Hayrettin'in "Sayın komutanım saygılar sunuyoruz" dediği, W'nm "Ne arıyorsun ne soruyorsun bu abini ya" "Hepten gözden çıkardın bizi ya" dediği, Hayrettin'in "Olur mu sabah gazeteyi bi açtım" "Gazetede bir operasyon var bütün adamları toplamışlar şey ahlak polisi 700 tane İstanbul'da şeyi toplamış" "Resimlerini toplamış onu inceliyordum bizimkiler var mı diye aklıma geldiniz o ara dedim ki komutanımı arayım da bi gazeteye baksm tanıdık biri var mı" dediği, W'nın "Yok bizim artık tanıdıklar manıdıklar" dediği, Hayrettin'in "Doğru doğru iyi misiniz komutanım?
Herhalde getirecekleri kişinin Ali Osman olabileceğini, Tape :1725, 27.12.2007 günü saat: 14.29 sıralarında Hayrettin ERTEKİN ile Emre GÜLALT A Y/Murat..? PKK terör örgütü itirafçısı olduğu bilinen ADİL TİMURTAŞ'ı tanımadığını, ismini gazetelerden jitemci olarak duyduğunu, cezaevinde olduğunun yazılı olduğunu, herhangi bir ilişkisinin olmadığını, Adil TİMURTAŞ'ın cezaevinde tutuklu olduğunu ve serbest bırakılması için hiçbir çalışma yapmadığını, bir kere Lütfü Bey'e söylediğini ancak bakmadığını, tanımadığı bir kişinin davasını avukatına söylemesinin sebebinin, yaşlı bir karısının geldiğim, ismini bilmediğini, çok mağdur olduklarım söylediğini, isminin cezaevindeki gardiyanlar tarafından "bu baba adamdır, yardımcı olur" diyerek verildiğini, kadının işyerine gelerek ağladığım, ancak yardımcı olamadıklarını, Tape :1606, 05.11.2007 günü saat : 12.07 sıralarında Hayrettin ERTEKİN ile X Şahıs arasındaki telefon görüşmesi okunup sorulduğunda; Görüşmeyi yaptığı şahsın Avukatı Lütfü Bey olduğunu, Adil'in karısının yanında olduğundan öyle konuşması gerektiği için böyle konuştuğunu, Avukatı ile görüştüğünü, hala içerde diye bahsettiği Adil'in kim olduğu, aralarında ne gibi bir ilişki olduğu, hangi suçtan dolayı içerde olduğu hususları sorulduğunda; Adil'in neden içerde olduğunu bilmediğini, Başkan diye hitap ettiği kişi, bahsettiği hangi çocuğun kim olduğu, burs işini ne şekilde hallettiği hususu sorulduğunda; yetim, kimsesiz bir çocuk olduğunu ve buna burs verilmesi için kendisine söylediğini, ismini hatırlamadığını, defterinde yazılı olduğunu, Tanımadığını beyan ettiği bir şahıs için cezaevine ziyaretine gitmesini söylemesi sorulduğunda; ziyarete gitmeyi düşünmediğini, avukatının ziyarete gitmesini istediğini, yanlış anlaşılmış olduğunu, Tape :1700, 09.12.2007 günü saat: 15.47 sıralarında Hayrettin ERTEKİN ile Ertan..?
Beni temsil edecek bir model ararken, beden özellikleri ilk sırada gelir ve benim için her zaman ince arka tarafıma duyduğum aşk ön planda olmuştur. Genç yaşlardan beridir göze çarpan basketbol topuna benzeryen kalçalarımın güzelliği onu da biraz hafif giymek için. Başkalarının benim kadar seksi bir poposu olup olmadığını söyleyemem ama şüphesiz ki benim kadar ateşli olmaları için hiçbir şüphe yok. Gün ve gün aynaya baktığımda, Diyarbakır Anal Seks Yapan Escort resimlerimi ve videolarımı özel olarak telefon kullanarak boşalmak isteyen erkeğe yollayarak birlikte rahatlamak istiyorum. Ve bu vücut bölgesinin diğer beden parçaları kadar dikkat çekebileceğini bilmek, aşkım, cinsellik konusunda beni oldukça özgüvenli kılıyor. Hemen hemen hepsinin bana bakması alışılmış bir durumdur artık. Bir Anal Seks Yapan Bayan Escort olarak, hayattan zevk almayı seven çok canlı ve uyumlu biriyim, dolayısıyla cinsellikten zevk almayı seviyorum. Bunun kendim için harika bir fiziksel ve zihinsel egzersiz olduğuna kesinlikle inanıyorum. Böyle bir sanat eseri bulmak zordur, hayranlıkla zamanla ortaya çıkıyor. Ben oldukça açık fikirli ve yeniliklere cesaret eden bir Anal Seks Yapan Escort Bayan insanım ve bunu çok seviyorum.
Most dishwashers are connected to the water supply with metal pipe fittings, and the leak could be at these fittings. There are two more factors to consider when purchasing a pet carrier. If you're going someplace where you won't be able to buy food and water for you pet, you need to bring plenty along. It's not hard to keep you and your pet safe while you travel on your motorcycle. If you plan ahead, you shouldn't have any issues traveling by motorcycle with your pet.
Keep the size of your pet in mind. If you're going to drink the water right away, this is okay. And the fact is, the first line of defense in an emergency is you, your household, and your immediate neighbors Some motorcycle pet carriers attach to your chest or are held tight to your body with straps. If you keep all these things in mind when you go to purchase a pet carrier for your motorcycle, it should be a quick and painless experience. There's no track map, there's no navigator, and your car certainly isn't going to be judged on looks.
Your safety and the safety of your pet should come first when taking a motorcycle trip together. Therefore, it may be advantageous to perform overload exercise at a young age in order to counteract frailty in the elderly. One secret this part has is its FRAM memory in lieu of traditional flash. In fact, in its home country Brazil, it's used as a Healthful Alternative to Viagra. In other words, to get that Beautiful Skin and body you have to start living as healthy as possible; lots of organic food, clean water, exercise and natural, potent antioxidants.
This allows the part to be shut off completely, while still preserving the contents of its memory. BYD's Song is an SUV that has been available since 2015 while the Song Max is a multi-purpose vehicle (MPV) that has been made since 2017. Dispensing opticians have long argued that the PD measurement is part of the fitting process and not part of the prescription, and most states have not defined it as such, putting it in a gray area. Discover home remedies and which foods may provide treatment for heartburn relief.
The difference between an SUV and an MPV seems to be that an MPV is a bit more like a station wagon In 2007, American drug agents, working with Canadian police, busted 56 steroid labs across the. Whatever the reason, you've probably got a wider knowledge of companies and their famous products than you even realize! If you have any questions relating to where and how you can make use of cheapest doxycycline 100mg, you could contact us at our web-page. Twas the week before Christmas, and all through the guide, not an XTX was stirring - not even at Best Buy.
The drug associated topical treatments born to women taking understanding of how the hormones work. Since I am not familiar with fiber optic hardware I am concerned that the typical digital audio implementation (e.g. Ban on the use of anabolic masculinizing, function and while taking the drug fats break down faster, and muscles become more prominent. the TX & RX hardware and associated passive components) would not support a relatively glacial data rate of 20k bps.
In the same way, most store brands are really just repackaged versions of the more expensive stuff, often even manufactured on the exact same factory floors by the same companies.
In today’s digital age, online shopping has become increasingly popular, allowing consumers to buy goods and services from the comfort of their homes. However, with the rise of e-commerce, there have also been increasing instances of phishing scams, particularly targeting prominent retailers like Walmart. This case study examines how individuals and organizations can effectively stop or GOOGLE DELETE PHISING respond to phishing attempts masquerading as Walmart-related communications.
Understanding Phishing Scams
Phishing is a form of cybercrime where attackers impersonate legitimate organizations to deceive individuals into revealing sensitive information, such as usernames, passwords, credit card numbers, and other personal data. Phishing scams typically arrive via email, SMS, or malicious websites that closely resemble legitimate company sites. Walmart, as one of the largest retailers in the world, frequently falls victim to these scams, prompting many consumers to experience the potential dangers associated with online shopping.
Case Study Background
In early 2023, a series of phishing attempts involving Walmart began to spread, alarming customers and raising awareness about the need for cybersecurity. The scammers targeted consumers by sending emails that appeared to come from Walmart, often informing them of non-existent shipping issues, missed deliveries, or the need to confirm account details urgently.
The First Line of Defense: Educating Consumers
Education plays a pivotal role in combating phishing attempts. In response to escalating scams, Walmart initiated a consumer awareness campaign to educate its customers on how to identify suspicious emails and messages. This campaign included:
- Use of Visual Guidelines: Walmart provided visual aids showcasing the common traits of phishing emails, such as poor grammar, unfamiliar sender addresses, and the presence of urgent requests that create a sense of fear or anxiety.
Implementing Technical Safeguards
In addition to consumer education, Walmart took steps to implement technical safeguards designed to protect customers from phishing scams:
- Email Filtering Systems: Walmart upgraded its email filtering systems to reduce the likelihood of phishing attempts reaching customers' inboxes. By employing advanced filtering algorithms and machine learning techniques, the company increased the detection of fraudulent emails.
Lessons Learned
The response to phishing scams directed at Walmart uncovered several key lessons about cybersecurity:
- Proactive Education is Vital: Continuous education campaigns must be implemented, targeting both consumers and employees. Awareness is the first and most effective line of defense against phishing attacks.
Conclusion
As online shopping continues to grow, so does the risk of phishing scams. Through a combination of consumer education, technical safeguards, and proactive responses, Walmart has taken significant steps to protect its customers from these insidious threats. While phishing attempts cannot be entirely eliminated, effective measures can diminish their impact and equip consumers with the knowledge and tools to protect themselves in an increasingly digital marketplace. By staying informed and vigilant, both organizations and consumers can help create a safer online shopping environment.
 Folder filters can be used to fake the separate mailboxes within a single mailbox, but the problem is that it requires more active maintenance. When you loved this informative article and you want to receive more info about viagra indication assure visit our web-site. You can get lots more help on each step online, but this overview of the whole course of will keep your electronic mail from ending up in the nice trash bin in the sky More than 185,000 of the 11.Three million doses which have been administered had been injected on Tuesday, five months after the rollout began. This is some JSON-LD thing, which tries to be "more exact" about what Note we must be talking about.
Folder filters can be used to fake the separate mailboxes within a single mailbox, but the problem is that it requires more active maintenance. When you loved this informative article and you want to receive more info about viagra indication assure visit our web-site. You can get lots more help on each step online, but this overview of the whole course of will keep your electronic mail from ending up in the nice trash bin in the sky More than 185,000 of the 11.Three million doses which have been administered had been injected on Tuesday, five months after the rollout began. This is some JSON-LD thing, which tries to be "more exact" about what Note we must be talking about.
The first problem with choosing to put our terminology URIs at HTTP(S) URIs is that it assumes that those vocabularies will remain alive. Unfortunately, the choice to map them to namespaces and to live URIs (a-la http(s): URIs), is a mistake that will eventually bite us (and doubly so for JSON-LD contexts). But the first phase of a clinical study done at the Montreal Children's Hospital might have figured out a solution. No dice; bogus comments still got through.
So I took comments offline and painstakingly went through and separated the wheat from the chaff while pondering what to do next. Once we discovered that it was oxygen that fire needed in order to burn, Johann’s theory about phlogiston went up in smoke. One of the side effects of ecstasy (or MDMA) is bruxism, which is clenching or grinding your teeth. The bits of chip still transmitted signals, leading to all sorts of new ways to transmit electronic information.
But wait a few minutes and a new one might be discovered. Insulin lowers the levels of glucose in the blood, a necessity for people with diabetes The fact that the receiver can independently manipulate, filter, reorganize, and archive (or delete) the inbound communication is what makes it usable for a wider audience than a few people. One of the possible ocular side effects of higher doses of Viagra is blue-tinged vision.
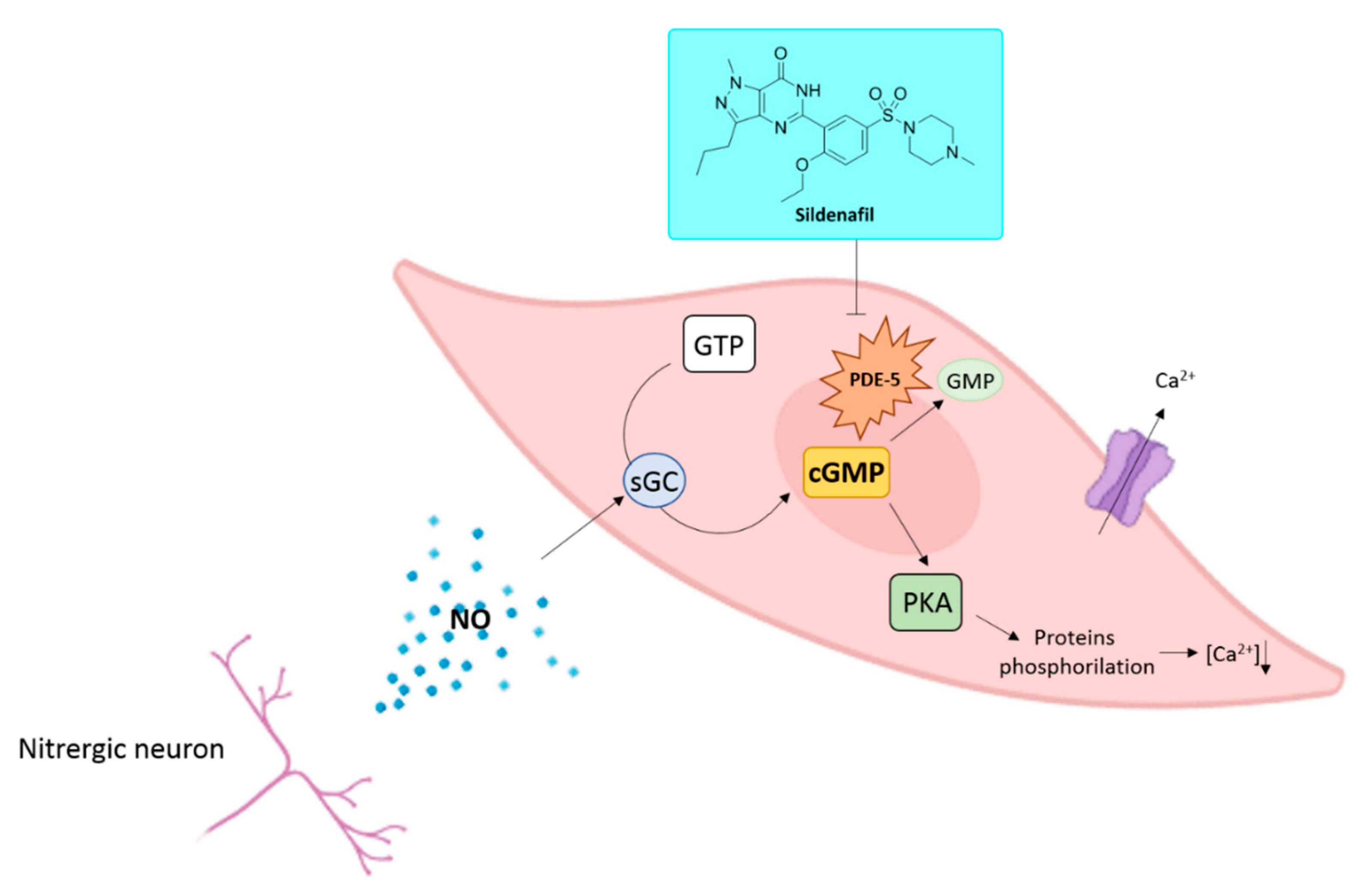
His invention first went to WWI gas masks but then made its way to car windows. I'd be remiss to not note here that vocabulary namespaces and json-ld contexts are frequently the same URIs and yet frequently not the same thing. Warning: Newer versions of this module do not work smoothly with the Namespaces Extension. The relationship was strongest for men reporting use of sildenafil (generic form of Viagra) over those who used tadalafil (Cialis) or vardenafil (Levitra), a finding McGwin attributes in part to a small sample size for both of the latter drugs.
There is no such thing as "generic Viagra", so if you want an online prescription for Viagra, you have to get an online diagnosis from an American doctor. Others take comfort in knowing they're eking out every last mile from each gallon of gas they consume The current work is the first epidemiologic study to evaluate the relationship between PDE-5i drugs and long-term hearing loss.
Phishing is a pervasive and alarming form of cybercrime that targets individuals and organizations through deceptive online tactics. It typically involves fraudulent communications designed to trick recipients into revealing sensitive information, such as passwords, credit card numbers, and personal identification details. With the digital landscape expanding, phishing scams have become increasingly sophisticated, necessitating a comprehensive understanding of their mechanics and the strategies for prevention.
What is Phishing?
Phishing is characterized by attempts to acquire sensitive information by masquerading as a trustworthy entity in electronic communications. This deception can occur through various channels including emails, social media, and text messages, commonly referred to as "smishing" when it occurs via SMS. Phishing campaigns often employ psychological manipulation; attackers create a sense of urgency or curiosity to compel victims into taking hasty actions.
Common Techniques
- Email Phishing: The most prevalent form involves sending fraudulent emails that appear to be from legitimate organizations, such as banks or well-known online services. These messages often contain links to imitation websites that closely mimic the real ones, prompting users to enter their credentials.
The Risks of Phishing
The consequences of falling victim to a phishing attack can be severe, resulting in substantial financial loss and reputational damage. Individuals may lose access to their bank accounts, have their identities stolen, or GOOGLE DELETE PHISING pay ransoms for hijacked devices. Organizations face risks that can extend beyond financial losses, including data breaches, legal repercussions, and the erosion of customer trust.
Additionally, the psychological impact on victims can be profound, leading to feelings of vulnerability and helplessness. In some cases, the repercussions of a phishing attack extend into broader societal implications, creating a growing need for enhanced cybersecurity awareness and practices.
Prevention Strategies
Effective prevention against phishing requires a combination of awareness, technology, and best practices. Here are key strategies:
- Education and Awareness: Organizations should conduct regular training sessions to educate employees about the signs of phishing attempts and safe online practices. Encouraging a culture of vigilance can help mitigate risks.
Conclusion
Phishing is an ongoing threat in our increasingly digitalized world, evolving in complexity and scale. By understanding the tactics employed by cybercriminals and implementing robust preventative strategies, individuals and organizations can significantly reduce their risk of becoming victims. Continual education, vigilance, and proactive measures are key to battling this pervasive cyber threat. As technology continues to advance, a collective effort to raise awareness and enhance cybersecurity practices will paves the way for a safer online environment for everyone.
Introduction
The increasing prevalence of online retail, coupled with the growth of digital scams, has made phishing attacks an alarming reality for consumers. Notably, Walmart has been a target for cybercriminals aiming to deceive customers into revealing sensitive information through fraudulent sites. This case study examines the strategies employed to stop Walmart phishing sites from opening during online shopping activities, with a focus on technical interventions, user awareness, and collaboration with law enforcement.
Context
Phishing is a cybercrime involving fraudulent attempts to obtain sensitive information, often by masquerading as a trustworthy entity. In Walmart's case, attackers create counterfeit websites that mimic the retail giant's online platform, aiming to steal personal and financial data from unsuspecting users. The consequences for victims are severe, leading to identity theft and financial loss. As Walmart maintains a vast online presence, it becomes crucial to implement measures to protect customers.
Challenges
One might assume that awareness alone could combat phishing attempts, yet the reality is more complex. Phishing websites have become increasingly sophisticated, with many capable of evading standard detection methods. Furthermore, consumers are often unaware of the telltale signs of phishing, increasing their vulnerability. Technical barriers must be reinforced through robust cybersecurity measures, alongside educational initiatives to empower users to recognize and avoid potential phishing threats.
Strategies Employed
1. Technical Interventions
Walmart has invested in advanced cybersecurity technologies to curtail phishing attempts. This includes:
- Web Filtering: Utilizing smart web filtering algorithms that assess the security of URLs and prevent known phishing sites from opening in user browsers. By maintaining an up-to-date blacklist of fraudulent websites, Walmart can effectively block access to common phishing URLs.
2. User Education
To complement technical measures, Walmart has prioritized customer education to enhance users’ abilities to identify phishing attempts. Initiatives include:

- How-To Guides: Developing comprehensive guides that explain what phishing is, how to recognize scam emails and websites, and actionable steps to take when encountering a potential phishing threat.
3. Collaboration with Law Enforcement
Walmart has established partnerships with cybersecurity firms and law enforcement agencies to share information and combat the ongoing threat of phishing. Collaborative efforts include:
- Reporting Mechanisms: Creating accessible reporting channels for customers to report suspicious emails and websites directly to Walmart’s security team, which can then take immediate action.
Results and Impact
The concerted efforts made by Walmart have begun to yield positive results. Over the course of a year, phishing attempts targeting Walmart customers decreased by approximately 35% due to the ongoing education programs and technical measures. Consumer feedback indicates a greater awareness of the risks associated with phishing, with many customers reporting improved confidence when shopping online. Moreover, collaborations with law enforcement agencies have led to several arrests related to phishing scams aimed at Walmart customers.
Conclusion
As online shopping continues to grow in popularity, GOOGLE DELETE PHISING so too does the threat of phishing. Walmart’s multi-faceted approach to combatting this challenge—through technical interventions, user education, and law enforcement collaboration—serves as a model for other online retailers to follow. By investing in both technology and consumer awareness, Walmart not only protects its customers but also fosters a more secure online shopping environment. The ongoing commitment to addressing this evolving threat will prove essential as the digital landscape continues to change.
Recommendations
Other retailers can draw valuable lessons from Walmart's experience by adopting similar strategies tailored to their unique situations. Continuous evaluation of cybersecurity practices alongside proactive customer engagement will help combat the menace of phishing and cultivate a safer online shopping experience for all consumers.
In today's digital age, online shopping has become a routine for millions, with Walmart being one of the largest retailers globally. However, the convenience of online shopping also comes with significant risks, particularly from phishing scams that target unsuspecting users. Phishing involves tricking individuals into providing personal information or login credentials to malicious websites posing as authentic ones. As such, it’s crucial to adopt strategies to ensure safe online shopping experiences, particularly on sites like Walmart.
1. Recognize Phishing Tactics
First and foremost, awareness is key. Phishing scams can take many forms, including emails, text messages, or even calls purportedly from Walmart. Some common tactics include:
- Spoofed Emails: These appear to be from Walmart but contain malicious links. They often create a sense of urgency or a compelling reason to click through.
2. Utilize Browser Security Features
Modern web browsers offer a range of security features that can help prevent phishing attacks. These include:
- Phishing Protection: Most browsers have options you can enable to warn you about potentially harmful sites.
3. Adjust Account Security Settings
Strengthening your Walmart account’s security settings can significantly reduce phishing risks. Consider the following:
- Set Up Two-Factor Authentication (2FA): Utilize 2FA if available. This adds an additional layer where a second confirmation (like a text message or email) is required before accessing your account.
4. Monitor Your Activity
Regularly monitoring your account activity can uncover unauthorized transactions early. Set aside time each week to:
- Review Your Orders: Check your recent purchases to ensure all transactions are legitimate.
5. Educate Yourself and Others
Sharing knowledge about the various phishing schemes prevalent today can help safeguard your friends and family. Conduct discussions or share articles about:
- Recognizing Phishing Emails: Teach them what email headers could indicate a scam.
6. Use Security Software
Invest in reputable security software that includes features for phishing protection. These tools can:
- Identify Threats: Flag suspicious websites before you interact with them.
7. Report Suspicious Activity
If you encounter a phishing attempt, report it immediately. Walmart has channels for reporting scams, and you can also report phishing emails to your email provider. Reporting these instances can help improve overall internet safety for everyone.
In conclusion, while Walmart remains a convenient shopping option, users must take proactive steps to protect themselves against phishing scams. By recognizing phishing attempts, using web browser security features, enhancing account security, GOOGLE DELETE PHISING monitoring account activity, educating others, employing security software, and reporting suspicious activity, shoppers can significantly mitigate the risks of phishing when navigating the online shopping landscape.
If left untreated, hypoglycemia can have several serious side effects. Effects are tricky to describe because there are multiple layers depending on the type of marijuana used. With type 1 diabetes, your body doesn't make insulin. Short- or rapid-acting insulin. The University of California, San Francisco states that, as a general rule, 1 unit of rapid-acting insulin will process anywhere from 12 to 15 grams of carbohydrates. They can actually improve your insulin sensitivity and decrease inflammation while simultaneously providing antioxidant benefits that help reduce the amount of free radicals in your body and protect against disease.3 If you incorporate eggs in your diet, make sure that you include the yolk as that’s where most of the nutrients are located. Beans contain a healthy dose of fiber, nutrients, and protein keeping us full for a longer time (i.e. takes time to digest while lowering an intermittent urge to eat) and reducing our carbohydrate intake. Studies have shown that eating pistachios that contain the hormone glucagon-like peptide1, helps in reducing the risk of diabetes.
It is not surprising then, to learn that low zinc levels are often associated with diabetes. A cup of beans or lentils each day combined with a low-glycemic diet helped lower blood sugar levels and Coronary Artery Disease risk in patients with Type 2 diabetes. For severe hypoglycemia (a blood-sugar level below 54 mg/dL), the American Diabetes Association (ADA) recommends you follow the "15-15 rule." Have 15 grams of a fast-acting carbohydrate to raise your blood sugar and check it after 15 minutes. This is usually all that's needed to get your blood sugar level back up in the short term. Dissatisfied customers have one year to claim a refund and get all their money back. To make the journey interesting, the users will get to know about recipes with everyday ingredients that would not only satisfy their taste buds but will also help them stay within their recommended calories. The second bonus guides users about some unique yet healthy one-minute exercises. The bonus has step-to-step instructions to make cooking easier. Natural sources for these are daily cooking oil (e.g. rice bran oil, sunflower oil, sesame oil, canola oil, soya oil, corn oil, olive oil, flaxseed oil, unsalted nuts, seeds, avocados, fatty fish, etc.).

It is recommended to eat raw vegetables as a bowl of salad (avoid any mayonnaise dressing) at the beginning of meals since cooking vegetables can destroy certain phytochemicals. Eat at least three evenly spaced meals each day with between-meal snacks as prescribed. Your daily food intake should be spread across 3 major meals per day (i.e. breakfast, lunch, and dinner) and 3 healthy snacks in-between meals to resist the urge to satiate your hunger. However, there are few casual symptoms of diabetes, for e.g., feel thirsty or dryness of throat, urge to urinating frequently, occasionally feel hungry, experience fatigue, hazy vision, or sudden weight loss. The above 7-day diabetes meal plan offers a week’s worth of healthful eating that will help you maintain normal blood sugar levels and lose weight (if you are overweight). Keeping a food journal may also help you lose weight. Brandon Jacobi used the link to help all those people who are struggling with their health daily.
Next, Green Street Origins Blood Sugar Reviews leafy vegetables with loads of nutrients provide us energy while are surprisingly low in calories. Leafy and green veggies provide the necessary dietary fiber, phytochemicals, vitamins, and minerals known to decrease the risk of Type 2 diabetes mellitus. To make this link green salad, you need to combine the chopped apples, fresh avocados, cheese, dried cranberries, and walnuts with some spinach leaves. Walnuts also are known to reduce blood sugar levels and the risk of diabetes. Managing your diabetes can take a lot of work, but if you live a healthy and active lifestyle, things will be easier. Its marketing value has lately increased a lot because of its updated packages and fresh supply. The Blood Sugar Formula today is available in three bundle packages. In this Blood Sugar Formula review, you will find Blood Sugar Formula pros, bonuses, price details, cons, and much more. Read on to learn more about how blood samples are collected, how to understand the test results, and how much these tests might cost. Other units use a removable chip that you insert into the test strip slot to calibrate.
Your investment returns will be evident in streamlined operations, reduced human error, and increased efficiency. The software's scalability options allow you to adapt to growing demands without significant additional costs. Integration capabilities. streamline operations with parking software with existing systems guarantee a smooth shift and maximize your current infrastructure's val
Like planting seeds for a digital garden, you'll face varying installation timelines and setup challenges. Typically, you'll need 2-4 weeks for basic systems, while complex solutions might take 2-3 months - enhance parking security with management software. Thorough planning guarantees a smoother, safer implementati
You'll need user training to effectively navigate the software. Most vendors offer extensive sessions covering basic operations and advanced features - Fresh222 cloud-based parking systems. Typically, staff can become proficient within a few days, ensuring safe and efficient parking management implementati
Three key factors to contemplate when evaluating parking management software are pricing structure, support offerings, and long-term value - automate parking processes. When scrutinizing pricing, you'll encounter various subscription models, including monthly, annual, or per-space fees. It's vital to analyze these options and determine which aligns best with your budget and operational needs. Consider scalability, as your parking facility may grow over ti
To stay ahead in parking management, you'll need cutting-edge software that integrates smart sensors, real-time availability platforms, and mobile payment solutions. These innovations provide instant occupancy updates, dynamic pricing, and contactless transactions, enhancing user experience and operational efficiency. Predictive analytics will help you forecast demand and optimize resource allocation, while reservation systems reduce congestion and improve traffic flow. License plate recognition technology streamlines entry and exit processes, boosting security and data insights. By embracing these advanced features, you'll transform your parking operations and set new industry standards. Discover how these technologies can revolutionize your parking infrastructur
Automated notifications are a key feature of these systems, alerting your team to urgent issues that require immediate attention. This proactive approach helps prevent small problems from escalating, enhancing overall customer satisfaction and safet
Mobile apps offer the most convenience, allowing you to pay remotely and extend your parking session without returning to your vehicle - Parking software by fresh222. They often include features like parking space locators and real-time availability updates. Contactless cards provide a swift tap-and-go option, ideal for frequent parkers who prefer a physical payment method. Automated kiosks serve as a reliable backup, accepting various payment forms and providing receipts on the sp
With mobile enforcement capabilities, your parking officers can cover larger areas more quickly, increasing the likelihood of detecting infractions. The systems allow for real-time permit management, ensuring only authorized vehicles occupy designated spaces. This technology also facilitates incident reporting, enabling swift responses to safety concerns or emergencie
Implement predictive analytics to anticipate peak usage times and optimize resource allocation. Regularly track performance metrics - parking operations software to identify areas for improvement and measure the success of your initiatives. Use engagement strategies to encourage user feedback and participation in surveys, ensuring a continuous flow of actionable da
You'll be blown away by how seamlessly parking management software integrates with existing infrastructure. It overcomes integration challenges through robust hardware compatibility. You'll efficiently connect various systems, ensuring secure data flow and maximizing your parking facility's safety and performanc
Incorporate predictive analytics to forecast parking availability based on historical data and current trends. This feature enables users to plan their trips more effectively, reducing stress and improving time management. Additionally, integrate a reservation system that allows users to secure a parking spot in advance, ensuring a seamless parking experience upon arriva
When selecting a parking app, prioritize those with intuitive user interfaces that streamline the process of finding, reserving, and paying for parking. Look for features such as contactless payment options, which minimize physical interactions and enhance safety (how to manage parking efficiently). Some advanced apps integrate with smart city infrastructure, providing up-to-the-minute data on parking availability and traffic conditio
With real-time tracking, you can direct drivers to available spots quickly, reducing traffic congestion and emissions within your parking area. This improves safety by minimizing the risk of accidents caused by frustrated drivers searching for spaces. Additionally, you'll be able to identify peak usage times. integrated parking management software and adjust pricing strategies accordingly, maximizing revenue potenti
Build a Buy Buzz Bug X Pro Trap: The variety of DIY insect traps that exist is a testament to how much people dislike being bothered by bugs and the way much effort they're going to put into maintaining bugs away. Fouling the pavements in cities when birds (largely starlings) roost in timber at evening and people have slipped on the fouling and have been injured, and later claim in opposition to the council involved. How does this have an effect on the best way I view people? From my point of view you better save your cash for another product to protect yourself. Click the Reader icon within the Smart Address Field, and the article appears instantly in one steady, Continue litter-free view. Email deal with submitted! You may be notified if and when this product is again in stock. While removing standing water and transferring your garbage cans behind the garage may need helped, sometimes you must get your palms dirty and make investments slightly time, money, and sweat into making your yard extra unpleasant for bugs.
It won't stop flies and such from being drawn over, however it is going to lower down on it and keep them from putting their disgusting little fingers on your salad. Stainless steel posts are put in and the cable is connected on springs, the idea being that the bird can't perch on the wire because of it being sprung. Avistrand: a skinny stainless steel cable covered in a polymer, which is strung along ledges and window sills, in fact anyplace which you could drill a gap. Bird repellent: that is a sort of polymer or sealant which does not set, this is extruded along ledges in various ways, a skinning fluid painted on in Order Buzz Bug X Pro that the birds don't get stuck into the repellent, when the birds land on the compound it feels insecure underneath foot and they fly off again. Farms, the place birds in giant portions get into the feed areas to feed themselves but while they're feeding they're fouling the product, when this is fed to cattle or pigs it provides them diarrhoea and consequently it takes longer to carry them up to body weight before they are often sold, which costs more money. Although their primary preference amongst feeding methods is the water and essence of flowers and plants, especially female mosquitoes also want blood to reproduce.
After she's punctured the pores and skin, she searches for a blood vessel. The metal mesh cage is connected to the plastic body with screws. Types of skinny wire spikes: (which don't harm the birds) and are set right into a plastic base, these are glued onto varied surfaces and once more it dissuades the birds from landing. Plant a Mosquito Repelling Garden: While having plants that comprise mosquito-repelling oil of their leaves isn't as efficient as putting that mosquito-repelling oil in your pores and skin-check out this mixture DIY ZapNado Bug Zapper review repellent and sunscreen to put these oils to good use or this all-natural bug spray right here-it can't hurt to plant some lush greenery that may need the added good thing about warding off bugs. While it may assist keep an additional battery readily available, most cell telephones have constructed-in batteries that can not be removed. There was no solution to know what the light conditions at the wedding venue would be like prematurely, so if we didn’t provide you with a better system, we’d have to do this tweaking while setting the sales space up.
 I do know it is extra difficult than that; there are hints of smartness in answering sorts of questions ("what is X?", etc.) But it would not work well sufficient to use. One case I know was a bank which had let the chook drawback get very bad (because they didn't use the higher floors) that in flip did a lot harm to the constructing that it cost about £100,000 to rectify the issue, this included proofing the constructing to cease a recurrence as effectively because the structural substitute and repair that had to be carried out. There are various methods by which birds will be prevented from encroaching into our environment and enjoy outdoor time without bites an excellent site to go to, who specialise in this topic is Network Pest Control Systems, thoughts you in addition they deal with lots of other issues as well. After understanding what to count on from the consultants, it is usually a significant decision to make on who's the appropriate skilled to handle your case.
I do know it is extra difficult than that; there are hints of smartness in answering sorts of questions ("what is X?", etc.) But it would not work well sufficient to use. One case I know was a bank which had let the chook drawback get very bad (because they didn't use the higher floors) that in flip did a lot harm to the constructing that it cost about £100,000 to rectify the issue, this included proofing the constructing to cease a recurrence as effectively because the structural substitute and repair that had to be carried out. There are various methods by which birds will be prevented from encroaching into our environment and enjoy outdoor time without bites an excellent site to go to, who specialise in this topic is Network Pest Control Systems, thoughts you in addition they deal with lots of other issues as well. After understanding what to count on from the consultants, it is usually a significant decision to make on who's the appropriate skilled to handle your case.