Site blog
In the age of digital communication, online phishing has emerged as one of the most persistent and damaging threats to personal and organizational security. Phishing is a form of cybercrime where attackers attempt to deceive individuals into providing sensitive information such as usernames, passwords, credit card numbers, and bank details. This article will delve into the mechanics of phishing attacks, their various forms, the impact they have on individuals and organizations, and measures that can be taken to protect against such threats.
What is Phishing?
Phishing typically involves an attacker masquerading as a trustworthy entity in electronic communications. The most common vector for phishing attacks is email, where the attacker sends messages that appear to be from legitimate sources, such as banks, online service providers, or well-known brands. These emails often contain links to fraudulent websites designed to look like the legitimate ones, tricking victims into entering their personal information.
While phishing is historically linked to email, the problem has evolved over the years. Attackers now use various methods to reach victims, including social media platforms, instant messaging, and even phone calls, adding a layer of complexity to detection and prevention.
Different Types of Phishing
- Spear Phishing: Unlike traditional phishing attacks that target a large number of people, spear phishing is personalized and aims at specific individuals or organizations. Attackers may gather information from social media profiles or other publicly available resources to create tailored messages that increase the likelihood of success.
The Impact of Phishing
The consequences of phishing can be severe. For individuals, falling victim to a phishing attack can result in identity theft, financial loss, and significant emotional distress. For organizations, the ramifications are even graver—data breaches can lead to substantial financial losses, erosion of customer trust, legal penalties, and damage to brand reputation. According to a report from cybersecurity firms, phishing accounts for a majority of data breaches. Organizations have found themselves investing heavily in cyber defense mechanisms as a direct response to these threats.
Recognizing Phishing Attempts
Spotting a phishing attempt can be challenging, especially as attackers constantly refine their techniques. However, there are several red flags that can help individuals and organizations identify potential phishing attempts:
- Unusual Sender Email Addresses: Attackers often create email addresses that closely resemble legitimate ones but may contain subtle misspellings or additional characters.
Prevention Measures
To effectively combat phishing, individuals and organizations must adopt a proactive approach. Here are some best practices:
- Education and Training: Regular training sessions on identifying phishing attacks can equip employees with the knowledge they need to recognize threats before they escalate.
Conclusion
As the digital landscape continues to evolve, so do the tactics employed by cybercriminals. Phishing remains one of the most common and dangerous forms of cyberattacks, but by understanding the methods used, recognizing warning signs, and implementing effective preventive measures, both individuals and organizations can defend against this pervasive threat. Awareness and vigilance are essential in safeguarding sensitive information in today's interconnected world.

The Rise of Self Vacuum Cleaners: Revolutionizing Home Maintenance
In the busy world of today, time efficiency and convenience are paramount, specifically in household tasks. Among the many developments in domestic innovation, self vacuum cleaners have emerged as a revolutionary innovation. With their capability to automate cleaning tasks and adapt to different environments, these devices are ending up being important in numerous homes. This short article digs into the features, benefits, and considerations of self vacuum, supplying a comprehensive overview for potential purchasers.
What is a Self Vacuum Cleaner?
A self good robot vacuum, typically referred to as a robotic vacuum, is a home cleaning gadget designed to operate autonomously. Using advanced technology such as expert system, sensing units, and sometimes even mapping capabilities, these vacuums can navigate around a home, preventing barriers, cleaning different floor types, and returning to their docking station when their battery runs low.
Secret Features of Self Vacuum Cleaners
self best inexpensive robot vacuum (https://algowiki.Win) come equipped with a range of functions that improve their performance and user experience. Here are some of the most noteworthy characteristics:
| Feature | Description |
|---|---|
| Navigation Technology | Uses sensing units and cameras to map the room and prevent challenges. |
| Setting up Capability | Users can configure cleaning times for benefit. |
| Dirt Detection | Some models can detect dirtier locations and concentrate on them. |
| Multi-Surface Cleaning | Reliable on carpets, wood, tiles, and more. |
| Integration with Smart Home | Can be controlled via smart devices and related to smart home systems. |
| Self-Charging Functionality | Instantly returns to the dock to recharge when needed. |
| HEPA Filters | Records great dust and irritants for much better air quality. |
Benefits of Self Vacuum Cleaners
The advantages of purchasing a self vacuum cleaner make them an attractive choice for families. Here are a few of the key advantages:
- Time-Saving: Automated cleaning frees up time for users to engage in other activities, from work to leisure.
- Constant Cleaning: Regular scheduled cleaning helps maintain a tidy living environment.
- Availability: Ideal for individuals with movement obstacles or those who struggle with standard vacuuming approaches.
- Energy Efficiency: Many models are created to operate on minimal energy, adding to lower energy bills.
- Advanced Cleaning Techniques: Enhanced functions such as HEPA filters help maintain indoor air quality, making them a healthier choice.
Factors to consider When Purchasing a Self Vacuum Cleaner
While self vacuum provide numerous advantages, there are several factors that buyers should think about before buying:
- Floor Type Compatibility: Evaluate whether the machine appropriates for the surfaces in your house.
- Battery Life: Look for designs with adequate battery life to cover your cleaning location in one charge.
- Size and Design: Consider a robot vacuum cleaner top 10's dimensions to ensure it can access tight areas under furniture.
- Upkeep Costs: Factor in the expense of filters, brushes, and other accessories that may require routine replacement.
- Noise Levels: Research designs known for quieter operation, specifically if home disruptions are an issue.
The Future of Self Vacuum Cleaners
As technology continues to advance, the capabilities of self vacuum cleaners are anticipated to progress. Future developments might include enhanced expert system, enabling these gadgets to find out and adapt to home cleaning preferences better. Additionally, boosted connectivity with IoT devices might offer users with smarter home integration and improved monitoring abilities, making cleaning much more smooth.
FAQs About Self Vacuum Cleaners
1. How do self vacuum navigate around furniture?
Self vacuum cleaners make use of a combination of sensors, video cameras, and mapping technology to browse around objects in their environment. They can spot barriers and adjust their course accordingly, making sure thorough cleaning protection.
2. Can self vacuum cleaners clean carpets efficiently?
Yes, many self vacuum cleaners are developed with brushes and suction power that can manage different floor types, including carpets. Some designs even change their suction settings based on the surface area they are cleaning.
3. Are self vacuum cleaners noisy?
The sound level of self vacuum varies by model. Nevertheless, many producers aim to create quieter systems, often operating at volumes comparable to that of a microwave.
4. Do self vacuum cleaners need upkeep?
Yes, self vacuum cleaners require regular upkeep, including cleaning or changing filters, clearing dust bins, and sometimes changing brushes to ensure optimum performance.

5. What is the typical lifespan of a self vacuum cleaner?
Most self vacuum have a normal lifespan of 3 to 5 years, depending upon the design, frequency of use, and upkeep practices.
Self vacuum embody the merging of innovation and practicality, changing how households approach cleaning jobs. With lowered effort and time investment, these devices raise the standard of home maintenance, creating a cleaner and more comfy living environment. As innovation advances, property owners can expect even smarter and more efficient cleaning solutions to emerge, even more improving the convenience and efficiency of home cleaning. Whether a busy expert or a family with kids, a self vacuum cleaner can unquestionably become a valuable partner in maintaining a neat home.
Découvrez ce site de paris qui propose une expérience inoubliable pour les fans de casino dans plusieurs pays de la région Afrique francophone tels que le Togo, la Côte d'Ivoire et bien d'autres. Une plateforme facile à utiliser avec des paris sportifs variés est offerte sur Android et via la version mobile.
Les Avantages de Mostbet
- Interface en français
- Disponible via APK pour Android
- Assistance en ligne à toute heure
- Limité aux joueurs majeurs
Paris Sportifs: Des Options Diversifiées
Mostbet offre une multitude d'options pour les paris sportifs, y compris le football et les eSports. Les paris en live vous permettent de parier pendant les matchs. Les taux de paris sont fréquemment mises à jour, offrant ainsi les meilleures opportunités de gains. Des compétitions locales sont également couverts pour une expérience personnalisée.
Explorez les Jeux de Casino sur Mostbet
mostbet casino propose une variété impressionnante de jeux pour les passionnés de casino. Parmi les jeux les plus populaires, vous trouverez Starburst. Des jeux de casino classiques sont également disponibles pour les joueurs expérimentés. Les joueurs peuvent un casino en direct avec de vrais croupiers.
Des Offres Avantageuses pour les Joueurs
mostbet casino propose des bonus intéressants pour les nouveaux joueurs, y compris un offre spéciale pour votre première expérience. Il y a qui vous permettent de essayer sans engagement. Des offres exclusives pour les joueurs réguliers permet aux joueurs de bénéficier d'avantages. Des bonus récurrents vous permettent de maximiser vos chances de gagner.
Des Méthodes de Paiement Adaptées
Les dépôts sont simples et sécurisés grâce à des solutions adaptées aux joueurs d'Afrique francophone comme les portefeuilles électroniques. Votre argent est en sécurité et les retrats sont rapides. Accédez à une interface de paiement simplifiée grâce à ces options adaptées à vos besoins.
Emportez votre Jeu Partout avec l’Application Mobile
La version mobile vous permet de gagner où que vous soyez. Les rappels en temps réel vous tiennent informé de chaque changement dans les cotes. L’application mobile est parfaitement adaptée pour une utilisation facile. Les ajustements instantanés permettent de rester informé.
Téléchargement et Installation: Commencez à Jouer
Pour télécharger l’application Mostbet, téléchargez directement depuis notre plateforme. Installez le fichier APK pour Android, puis autorisez l'installation depuis une source sécurisée. Dès l'installation, connectez-vous à votre compte et explorez vos paris.
Le site est la meilleure option pour ceux qui cherchent à parier et jouer. Rejoignez-nous dès aujourd'hui et profitez de promotions. Faites vos premiers paris sur ce site. Mostbet France
When diabetes is uncontrolled, it prevents glucose from entering cells for conversion into energy. The lack of energy sends signals to the brain, suggesting that more food is needed to bring energy levels back up. Instead of being used by your body, glucose builds up in your blood and your body is starved of energy. Whether you've been diagnosed with diabetes, and you want to make sure you have healthy HemoPulse Blood Sugar sugar levels, or you're suspicious as to whether you have the condition or not, two telling signs could be on your face. This is how you find out what your blood sugar level is at that moment in time. Michelle Schreiner's blood sugar was dangerously low when a friend called 9-1-1 and Gresham police and Gluco Maxum Review paramedics arrived to find her holding a syringe full of insulin. Use this calculator to check your body mass index (BMI) and find out if you are a healthy weight. More and more people with diabetes are choosing to use a flash glucose monitor to check their sugar levels.
Use it by itself or connect one of our partner’s physical activity trackers to have your exercises synced directly into the app. Hyperglycemia is diagnosed when blood glucose levels are higher than 100 mg/dL while fasting, higher than 180 mg/dL one to two hours after the start of a meal, or when your blood glucose level is higher than 200 mg/dL. Aim for at least 2 hours and 30 minutes a week of moderate-intensity aerobic activity, like walking fast or biking. It can also happen about 4 hours after a meal. Take a walk, especially 15 minutes after a meal. No matter how you choose to get your heart pumping, do it for at least 20-30 minutes a day. 4. Do You Get Too Little Exercise? Talk to your healthcare provider to get a better understanding of why this is happening and if you should be taking additional steps to stay healthy.

People with diagnosed diabetes should see their healthcare provider several times a year. In people with long-standing diabetes, it can sometimes cause irreversible skin changes. Dietary changes are an effective way to manage diabetes, especially for those with type 2 diabetes. While alcohol and sugary drinks are strongly advised against, other drinks like tomato juice are recommended. Some people prefer drinking kale juice as it is more effective and acts faster as compared to eating the vegetable. Muscle is heavier than fat, so weight loss is common in people with uncontrolled diabetes. Excessive urination also means that you are losing excessive amounts of water, which can contribute to weight fluctuations. In diabetic patients glucose level fluctuations are common and adjusting the insulin dose or other drugs can help resolve the problem. Over time, the persistent swelling can damage the retina, leading to a condition known as diabetic retinopathy, in which blurred vision and vision loss are common. If left untreated, hyperglycemia can lead to diabetic ketoacidosis, which is a life-threatening disease. It is a symptom of diabetes that can lead to extreme dehydration and kidney injury if your blood sugar is not kept in check.
But severe hypoglycemia can lead to a loss of consciousness and become life-threatening. Diabetes can affect the skin in different ways. Uncontrolled type 2 diabetes can shorten your lifespan in other ways. On average, the life expectancy of people with type 2 diabetes is six years shorter than nondiabetics. If you live with type 2 diabetes, Wellness Of Blood Review eating nuts five days a week may be just as critical for HemoPulse Blood Sugar your long-term well-being as regular exercise and checking your blood sugar. I’ll probably be doing it for years, I doubt that they’ll ever give them up even with the newer model." For the past five years Dr. Orzeck sought someone to begin making new units. However, research shows improving blood sugar control can add 3.8 years back. Uncontrolled high Stimula Blood Sugar Review sugar can weaken the body's immune system and make it harder to fight infections. This occurs when impaired blood flow to the foot not only increases the risk of infection but reduces the availability of immune cells to fight the infection. Sustained high blood sugar also increases your risk of complications that may be disabling.
Mostbet: Your Ultimate Betting Experience
In the dynamic world of online gaming, mostbet uz excels as an innovative platform offering unparalleled gaming solutions. With years of industry presence, we've mastered the science of combining exciting wagering with cutting-edge technology.
Our Competitive Edge
Massive range of sports markets covering over 50 sports disciplinesIndustry-leading payouts to boost your earning potentialRapid payments with numerous payment methodsGenerous reward system valued at up to $1000 for new players24/7 player assistance multiple languagesWant to join the winners' circle? mostbet now!
Diverse Entertainment Options
At mostbet bd, every player discovers their ideal game:
Live Wagering Hub
From football to table tennis, our sportsbook features 1000+ weekly matches with live streaming and cash-out options.
Real-Time Gaming
Immerse yourself our luxurious live casino with authentic tables hosting roulette rounds in 4K quality.
Virtual Games
Explore our cutting-edge eSports offerings with realistic animations and frequent events.
Mobile Gaming Revolution
Our mostbet Bangladesh mobile app provides smooth betting anytime, mostbet зеркало anywhere:
User-friendly design adapted for all screen sizesExclusive mobile bonuses inaccessible on desktopOne-tap entry to every service including live streamingAdvanced login options for mostbet বাংলাদেশ secure accessGet the app and mostbet Кыргызстан carry the excitement in your pocket! mostbet नेपाल
Security & Fair Play
Player safety is our focus:
Regulated by Curacao eGamingSSL encryption for financial operationsRandom number generator mostbet Azerbaycan systems for game integrityResponsible gaming tools such as deposit limitsBecome part of the family of millions of satisfied players worldwide! mostbet np
I use what I imagine a psychiatrist might call positive reinforcement - I recall times when I've won big time, I just how much and watch the videos of those races where my horse has won, and I read over my betting archives and records, all this to remind myself what has gone before the. On occasions I'd personally consider attending a brief spell away from betting altogether, to rid negative thoughts from my thoughts - after my grandfather died in 2001 I conducted exactly that, and lately back in February of this occurence year.
Among the premier league betting system, predicting the draw has become most simplest and so much easier to include. The only basis for this betting system is the favorite sides. The bettor should know how well his chosen teams perform and analyze the statistics of the two teams. Basically, if both teams are evenly matched there is really a greater chance that the two teams could settle to your draw. In case a good team is associated with a poor performer team then this betting product is not right for such program. This kind of betting system works effectively on teams about the same level of performance. However, predicting a draw powerful and be profitable for people who have more than sufficient regarding the playing teams.
The best benefit of something which? Well, there are two best parts, actually. The initial one is you do not have for being "high roller" to obtain the benefits for the slot club. When my wife and When i first got towards Mississippi Gulf Coast, we never played anything greater than penny slots. Still, every month, we'd get mailings from the สล็อตฝากถอนไม่มีขั้นต่ํา telling us i always had free money to play with. Personal computers didn't a bundle of money for playing at that level, but even $5 for free is better than $0 f-r-e-e.
Using this theory, the practitioners can play an online casino offering a promising bonus, obtain a profit a good amount approximate to the calculated value, and then move on to another สล็อตฝากถอนไม่มีขั้นต่ํา offering point kind of promise without incurring any loss . They will play one casino till tend to be satisfied that possible profit had been squeeze out, then hop onto another casino repeating the process there after which it another one and such. Hence the term.
There can be be the amount of who obtain a thrill of betting intended at somewhat of the button, for players similar the high roller slots are the most effective option. This is also open to people internet. Online casinos are always on the particular continual battle to cater on the various requirements for an increased roller player as irrespective of how always possibility that they go to a competitor these people do not get how they want.
The best thing about slots is that, it is very easy to predict which for this machines available are the best ones to play with. Determining the best slot is not new intercourse is a of the casino goers around the world. Especially when you usually playing the particular same casino, you can observe which of the slot machines give belly payout.
So, you'll be in along with one - the author of this system and it is possible to improve your betting almost immediately. This system gives the opportunity produce the same bets considering that professionals do and believe me that 1 thing that you'll be able to only win of!
For many decades now, slot games have been very popular in casinos. This is they slots do not only gives a better regarding recreation into the players yet can also allow the particular go home with associated with money after winning.
If you want to get into slotcar racing there is far you really should know. I encourage reading the rules and knowing what type of slotcar you want race. Many slot car tracks have times and days of each week that someone can place their car in and practice with their friends.
Playing online slots is one of one of the most fun issues that are situated on the affiliate. In fact, for some players internet means only 'Online Slot Machines'. Precisely is simple the fast and furious flash software that enables the online slot machines to present the real excitement like regarding land based casinos. The online slot game machines always be the same crazy and unpredictable as probably the most Las Vegas slot machines are.
Over confidence, laziness and indiscipline. Being long term successful punter is like swimming contrary to the tide. It will take an effort to stay still, increased effort to flex ahead which as soon when relax or slack from you start to go to backwards.
Slot games have been very popular in สล็อตฝากถอนไม่มีขั้นต่ํา s for times. Its popularity is due into the game's ability to provide gaining interest exciting involving recreation for a variety of casino guests. Slot machines are also able to make some people rich; this is the reason more and more people are fascinated to play slots you will find.
The next most important tip allow you avoid emptying your bank account is to set a limit on the amount you 're going to give. slot machines were designed, after, to keep people passionate. They are highly enjoyable. While playing, merchants also be too engrossed in the slot machine and never pay much care about the volume of money you've already invested. This is yet another big mistakes. There should become limit regarding how much an individual willing to spend, an excellent you reach that limit, you have enough self-control to leave. And remember, your winnings, as previously mentioned, donrrrt want to be part of this allowance.
Phishing is a form of cybercrime that involves deceiving individuals into providing sensitive information such as usernames, passwords, credit card details, and other personal data. This malicious tactic has evolved over the years into a sophisticated method of attack that leverages social engineering and technological advancements to exploit human emotions like fear, curiosity, and trust. As the internet continues to grow, so does the prevalence of phishing attacks, making it imperative for users to understand the nature of this threat, the techniques employed by attackers, and the methods for GOOGLE DELETE PHISING protection.
The term "phishing" is derived from the word "fishing," implying that cybercriminals are casting a net to catch unsuspecting victims. Typically, phishing involves the use of fraudulent emails or websites designed to appear legitimate, often mimicking well-known organizations such as banks, online services, or social media platforms. These communications usually contain urgent messages that prompt users to click on malicious links, which lead to sites that resemble authentic web pages.
One common type of phishing attack is spear phishing, where attackers target specific individuals or organizations with personalized messages. This approach increases the likelihood of success because the attackers gather information about their victims beforehand, making the content more convincing. For instance, they may reference current projects, mutual acquaintances, or legitimate business accounts, creating a false sense of security.
Another variant is whaling, which specifically targets high-profile individuals within organizations, such as executives or senior management. By using highly tailored messages, whaling attacks aim to extract sensitive corporate information or initiate fraudulent wire transfers. Given the potential financial repercussions and reputational damage, whaling poses a significant risk to companies and their stakeholders.
Phishing has also expanded beyond email, with the emergence of SMS phishing (smishing) and voice phishing (vishing). Smishing involves sending fraudulent text messages that prompt users to provide personal information or click on malicious links. Vishing, on the other hand, is executed through phone calls that impersonate legitimate entities, such as banks or government agencies. These methods leverage technology to reach individuals directly, increasing the persuasion factor in the communication.
The impact of phishing attacks can be severe. Victims may suffer financial losses, identity theft, and unauthorized transactions, while companies can face legal repercussions, loss of customer trust, and data breaches that compromise sensitive corporate information. According to the Anti-Phishing Working Group (APWG), phishing attacks have increased dramatically, with millions of phishing websites reported each year. This growth indicates a pressing need for effective countermeasures.
To combat phishing, it is essential for individuals and organizations to implement robust security practices. One of the first steps is to educate users about the risks associated with phishing and how to recognize potential threats. This education includes training programs that cover the common signs of phishing attempts, such as misspelled URLs, generic greetings, and suspicious attachments.
Another critical measure is the adoption of multi-factor authentication (MFA). MFA provides an additional layer of security by requiring users to confirm their identity through multiple means—such as a password followed by a unique code sent to their mobile device—making it more challenging for cybercriminals to gain unauthorized access.
Regularly updating software and security systems is also crucial. Organizations should ensure that all applications, operating systems, and anti-virus software are kept up to date to protect against known vulnerabilities exploited by attackers. Moreover, utilizing advanced email filtering solutions can help detect and block phishing attempts before they reach the user's inbox.
For individuals, verifying the authenticity of communications is vital. Users should take the time to hover over links to inspect their URLs before clicking, avoid providing personal information in response to unsolicited requests, and be vigilant about any correspondence that evokes a sense of urgency or fear. When in doubt, contacting the organization directly using official contact methods can help confirm the legitimacy of the communication.
In conclusion, phishing is a pervasive cyber threat that can lead to significant financial and personal losses if left unchecked. As technology continues to evolve, so do the tactics employed by cybercriminals. Therefore, understanding the nature of phishing, recognizing its various forms, and implementing effective security measures are essential in protecting oneself and one’s organization from this growing threat. Through education and vigilance, individuals and companies can significantly mitigate the risks associated with phishing and maintain a secure online environment.
In the age of digital communication, online phishing has emerged as one of the most persistent and damaging threats to personal and organizational security. Phishing is a form of cybercrime where attackers attempt to deceive individuals into providing sensitive information such as usernames, passwords, credit card numbers, and bank details. This article will delve into the mechanics of phishing attacks, their various forms, the impact they have on individuals and organizations, and measures that can be taken to protect against such threats.
What is Phishing?
Phishing typically involves an attacker masquerading as a trustworthy entity in electronic communications. The most common vector for phishing attacks is email, where the attacker sends messages that appear to be from legitimate sources, such as banks, online service providers, or well-known brands. These emails often contain links to fraudulent websites designed to look like the legitimate ones, tricking victims into entering their personal information.
While phishing is historically linked to email, the problem has evolved over the years. Attackers now use various methods to reach victims, including social media platforms, instant messaging, and even phone calls, adding a layer of complexity to detection and prevention.
Different Types of Phishing
- Spear Phishing: Unlike traditional phishing attacks that target a large number of people, spear phishing is personalized and aims at specific individuals or organizations. Attackers may gather information from social media profiles or other publicly available resources to create tailored messages that increase the likelihood of success.
The Impact of Phishing
The consequences of phishing can be severe. For individuals, falling victim to a phishing attack can result in identity theft, financial loss, and significant emotional distress. For organizations, the ramifications are even graver—data breaches can lead to substantial financial losses, erosion of customer trust, legal penalties, GOOGLE DELETE PHISING and damage to brand reputation. According to a report from cybersecurity firms, phishing accounts for a majority of data breaches. Organizations have found themselves investing heavily in cyber defense mechanisms as a direct response to these threats.
Recognizing Phishing Attempts
Spotting a phishing attempt can be challenging, especially as attackers constantly refine their techniques. However, there are several red flags that can help individuals and organizations identify potential phishing attempts:

- Unusual Sender Email Addresses: Attackers often create email addresses that closely resemble legitimate ones but may contain subtle misspellings or additional characters.
Prevention Measures
To effectively combat phishing, individuals and organizations must adopt a proactive approach. Here are some best practices:
- Education and Training: Regular training sessions on identifying phishing attacks can equip employees with the knowledge they need to recognize threats before they escalate.
Conclusion
As the digital landscape continues to evolve, so do the tactics employed by cybercriminals. Phishing remains one of the most common and dangerous forms of cyberattacks, but by understanding the methods used, recognizing warning signs, and implementing effective preventive measures, both individuals and organizations can defend against this pervasive threat. Awareness and vigilance are essential in safeguarding sensitive information in today's interconnected world.
What’s Hot in Casinos for 2025
Hello, mostbet Қазақстан thrill-chasers! Ready to explore the next big thing? The digital gaming scene is evolving fast, bringing exciting trends that deliver more fun. Discover what’s hot the casino landscape in 2025!
Crypto Casinos Take Center Stage
Crypto payments are taking over in gaming platforms. Litecoin and other cryptos offer fast deposits with minimal costs. Players love the anonymity and mostbet игры efficiency – no more slow processing for payouts! And, special coin rewards like free spins are popping up. Ready to go crypto?
The Rise of Next-Gen Live Gaming
Live-streamed gambling are bigger than ever, thanks to cutting-edge features. Blackjack with live hosts now includes dynamic overlays for a smoother experience. Immersive tech is also on the rise, letting you feel like you’re in a digital Vegas. Pure casino magic – mostbet hu!
Gamification: More Than Just Spinning
Gamification is spicing up casino apps. Earn badges as you play, or mostbet букмекер challenge others in daily quests. Loyalty programs now offer unique missions, making every bet feel epic. Who doesn’t love a challenge?
Casinos in Your Pocket
Gaming apps are everywhere in 2025. Play slots from your device with seamless apps. In-app alerts keep you on top with new games. No downloads needed – just log in and win. Ideal for зеркало мостбет quick sessions, right?
Responsible Gambling Takes Priority
Gaming sites are ramping up on responsible gaming. AI tools now track your spending and suggest time-outs to keep things balanced. Self-exclusion options are easier to use across reputable casinos. Stay in control – it’s the future of fun.
Ready to join the action? The online gaming scene is packed with new features. From crypto to gamified rewards, mostbet Bangladesh there’s something for everyone. Jump in at mostbet букмекер and mostbet Ukraine win big like never before!
The digital landscape is often fraught with threats, with cybersecurity companies like Avast at the forefront of protecting users from online scams. In a recent incident that has garnered widespread attention, Avast's online security software erroneously classified a legitimate website as a phishing threat, sending ripples through its user community. This mix-up has raised questions about the reliability of automated cybersecurity tools, their impact on businesses, and the rights of users navigating the internet.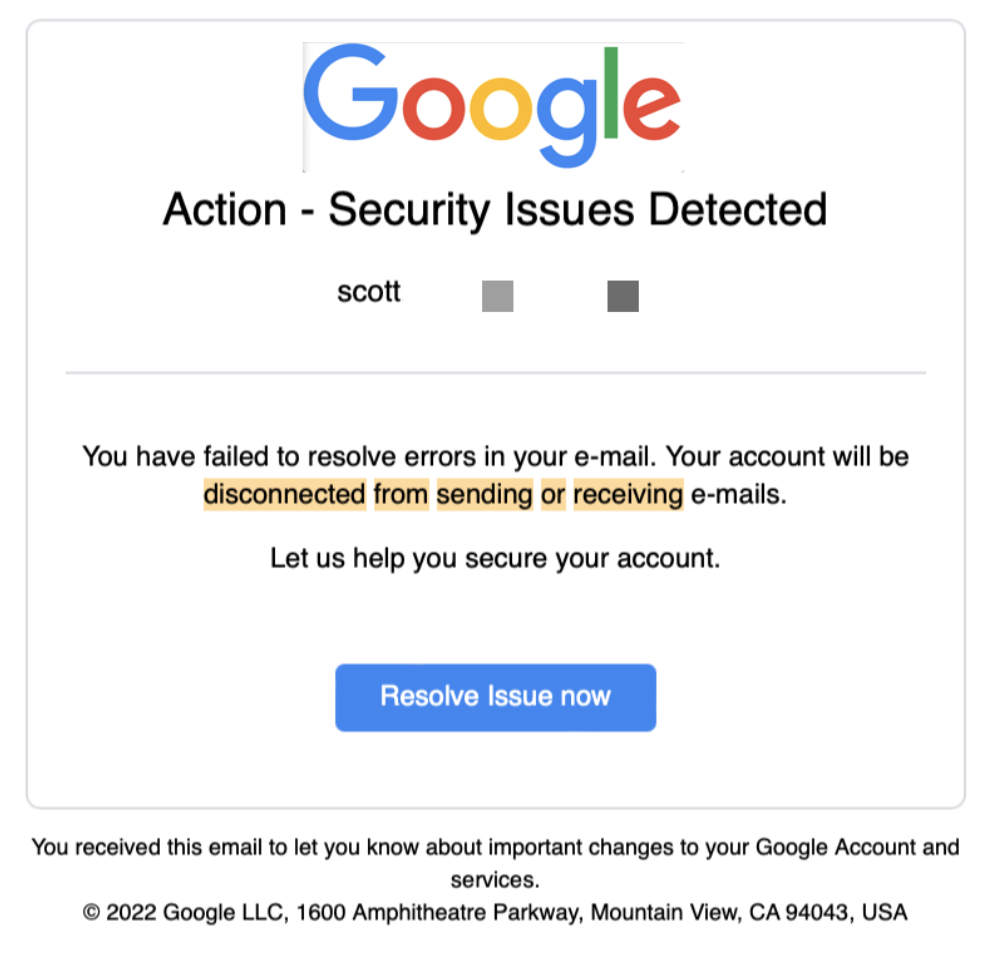
The incident occurred on April 15, when users reported that Avast had blocked access to the website belonging to Legit Web, a popular platform known for its user-friendly interface and commitment to customer service. Upon trying to access the site, users were met with a stark warning from Avast, which stated that the page was a potential phishing site designed to steal personal information. This alarmed many, particularly small business owners and freelancers who relied heavily on the platform for their operations.
Following the block, a wave of complaints flooded social media as users expressed outrage. Many users stated that they felt disheartened and frustrated by the incident, emphasizing the potential loss of revenue and trust in Legit Web. "Our whole business runs on that platform, and now we have to look for alternatives," shared Maria Lopez, a graphic designer whose clientele is largely based on projects from Legit Web. "It’s not just an inconvenience; it’s detrimental to our livelihood."
In response to the rising uproar, Avast released a statement acknowledging the error. The company explained that its automated security systems rely on databases and algorithms to evaluate the safety of websites. Unfortunately, the algorithm had mistakenly flagged Legit Web due to a combination of factors, including recent changes to its URL structure and an uptick in negative reports that, upon analysis, were unfounded. The statement reassured users that the incident was being investigated and that efforts were underway to prevent such occurrences in the future.
Phishing attacks continue to be a significant concern in the cybersecurity field, with hackers constantly devising new tactics to lure unsuspecting individuals into revealing sensitive information. Consequently, security software is critical in providing users with warnings about potentially dangerous sites. However, this reliance on automated systems has a flip side, as seen in this scenario where a legitimate website is misidentified as a threat.
Experts in the field suggest that such incidents bring to light the challenges inherent in automated flagging systems. "While automated systems can process vast amounts of data quickly, there's always a margin of error," stated Dr. Michael Roberts, GOOGLE DELETE PHISING a cybersecurity analyst. "When these systems are mistaken, the fallout can be significant, especially for businesses that depend on their online presence. It underscores the need for a hybrid system where automated tools are supported by human oversight."
The unintended consequences of this misclassification extended beyond individual users. Legit Web's representatives reported a substantial increase in customer service inquiries, as many users were panicked by the warning and sought clarification on whether their data had been compromised. The site’s creators swiftly initiated communication with Avast to resolve the issue and ensure that users were informed about the real situation.
Online businesses thrive on trust, and an automated phishing flag can damage that trust quickly. Some business owners expressed concerns that their reputation might suffer irreparable harm due to this incident. "We’ve spent years building our brand and reputation, and now we risk losing that due to a software blunder," said Tom Harris, the CEO of Legit Web. "We hope Avast rectifies this issue quickly and reinstates our site to avoid more unnecessary damage."
In the wake of the incident, it has become increasingly essential for users to remain vigilant, understanding that while cybersecurity tools are designed to protect them, they are not infallible. VPNs, firewalls, and antivirus software provide layers of security, but the onus is also on individuals and businesses to verify the legitimacy of sites before inputting sensitive information.
Cybersecurity companies must take these missteps seriously and work towards systems that reduce the chances of wrongful blocks in the future. As Avast works to rectify the situation and the dust settles, users are left navigating the complexities of online threats with a newfound understanding: the fight against cybersecurity risks is a continuous battle filled with uncertainties, even from those entrusted to safeguard us.
As the story develops, users and businesses alike will be watching closely how Avast handles its response and what measures it adopts to reassure its community that they are safe in their online endeavors.